Antivirus Graph: An Introductory Guide

Antivirus software has long been the first line of defense against malware. By scanning files and processes for known patterns, called signatures, it can quickly detect and block many common threats. However, today’s attackers are more adaptive. They use polymorphic malware, fileless techniques, and legitimate tools in unexpected ways to bypass static rules. These methods often leave no recognizable signature behind.
To stay ahead, antivirus systems need more than pattern matching. They need context. What process spawned the suspicious executable? Did it communicate with known malicious domains? Was the user logged in with elevated privileges? Answering these questions requires understanding how events are connected.
That’s where the antivirus graph comes in. An antivirus graph is a graph-based representation of endpoint activity. By modeling endpoint activity as a graph of related entities, such as files, processes, users, and network connections, security teams can analyze behaviors and relationships, not just isolated events. In this post, we explore how graph techniques can enhance antivirus systems: uncovering complex threats, connecting disparate signals, and guiding more effective responses. We’ll also discuss the practical challenges of adopting antivirus graphs and graph analytics and how PuppyGraph makes this approach accessible without overhauling your infrastructure.
What is an Antivirus Graph?
An antivirus graph is a dynamic, connected model that maps interactions between entities on a system—such as which process launched a child process, which files were accessed or modified, and which network destinations were contacted. In this graph, nodes represent key elements like processes, files, users, and IP addresses, while edges illustrate the actions or relationships between them, such as "spawned," "altered," or "connected to."
Unlike traditional approaches that view system activity as flat, isolated events in logs, the antivirus graph weaves these pieces into a cohesive, time-based structure. This reveals the flow of execution, enabling analysts and detection systems to trace complex chains of behavior—such as a suspicious process downloading a file and contacting a shady IP—that would be nearly impossible to spot in raw logs alone. By highlighting these patterns, antivirus graphs empower security teams to uncover and combat sophisticated threats like polymorphic or fileless malware.
Why Antivirus Graphs Matter in Modern Cybersecurity
Antivirus graphs provide a crucial evolution in cybersecurity by offering deep contextual insights that traditional methods often miss. To understand their significance, it's helpful to first consider the challenges and gaps in established security approaches, particularly the most common one: signature-based detection.
Limitations of Signature-Based Detection
Signature-based detection has been the foundation of antivirus software for decades. It works by comparing files, processes, or behaviors against a database of known threat “signatures”—distinctive patterns such as byte sequences, hash values, or command strings associated with malware. When a match is found, the system can block or quarantine the threat immediately.
This approach is fast, reliable, and highly effective against previously encountered malware. However, its strengths are also its biggest limitations.
First, it can’t detect new or modified threats. Malware authors frequently alter their code to evade detection. Even minor changes can produce a new hash that no longer matches the known signature. Polymorphic and metamorphic malware go further by changing their appearance every time they execute, making signature matching almost useless.
Second, it lacks context. Signature-based tools evaluate each object in isolation. They don’t consider how a file was delivered, which user executed it, what other systems it interacted with, or how it behaved after launch. Without this context, it’s easy to miss sophisticated, multi-stage attacks that look benign at each individual step.
Third, it struggles with fileless and behavior-based attacks. Many modern threats don’t drop a malicious file at all. Instead, they exploit trusted tools like PowerShell or run entirely in memory. These techniques often generate no signature and leave minimal forensic trace.
As a result, defenders relying solely on signature-based tools are left with blind spots. To address them, many security teams turn to endpoint detection and response, behavioral analytics, and increasingly, graph-based approaches that focus on relationships rather than static patterns.
Graphs Add What Antivirus Is Missing: Relationships
Modern threats don’t operate in isolation. They unfold across a sequence of actions involving multiple entities. A malicious script might be launched by a trusted process, connect to a command and control server, download a secondary payload, and attempt lateral movement. Each step might seem harmless individually. The danger lies in their connections. This is where graph modeling makes a difference.
In an antivirus graph, entities such as files, processes, users, and network connections are represented as nodes. Their interactions, such as process spawning, file modification, or communication between IPs, are captured as edges. Together, these form a structured view of behavior and relationships across the system.
Unlike rule-based or event-by-event detection, a graph-based approach highlights how different elements relate to one another over time and across machines. It can answer questions like:
- Did this executable originate from a suspicious email attachment?
- Which users ran this unsigned binary, and what other systems did they access?
- Do multiple infected machines share the same outbound connection pattern?
Antivirus graphs also support multi-hop analysis, meaning they can trace a full chain of actions—not just the immediate cause of an alert. This is especially valuable in post-compromise analysis, where understanding the full scope of an attack requires following its path through the environment.
For antivirus systems, antivirus graphs and graph analytics don't replace traditional detection. They complement it by providing the missing structure and context that can reveal stealthy or evasive threats. Even when signatures fail, relationships often expose the attack.
Example: Investigating Lateral Movement After Initial Compromise
Consider a case where an attacker gains access to a low-privilege user account through stolen VPN credentials. From there, they access a shared file server and discover a misconfigured script with hardcoded credentials. Using these credentials, they authenticate to a development VM, where they find SSH keys stored in plaintext. The attacker then uses those keys to connect to a production server and exfiltrate sensitive data.
Each of these steps might generate independent logs: a successful VPN login, a file access, an SSH session. Signature-based tools won’t detect anything malicious—because no known malware was executed, and every action was technically “allowed.”
But in an antivirus graph, the progression is clear: the compromised user accesses a file with credentials → logs into another system → retrieves additional secrets → connects to a sensitive server. This path exposes the escalation and privilege chaining that would be difficult to reconstruct manually. With graph queries, analysts can trace lateral movement through user accounts, credentials, and systems—uncovering the full impact of a breach that would otherwise remain hidden.
Key Use Cases of Antivirus Graphs
Integrating graph analytics with antivirus systems opens up a wide range of capabilities that go beyond simple file scanning. By analyzing relationships and behaviors, security teams can detect hidden threats, investigate incidents more thoroughly, and respond with greater precision. Here are several use cases where antivirus graphs add significant value.
Behavior-Based Threat Detection
Antivirus engines typically detect threats at the moment of execution or access. But many threats only reveal their malicious nature through a sequence of actions. An antivirus graph allows analysts to trace these behaviors as a chain, such as a macro-enabled document spawning PowerShell, which downloads and executes an unknown binary. Even if no individual step matches a known signature, the full path reveals the threat. Graphs expose rare or risky patterns that might otherwise go unnoticed.
Malware Campaign Linkage
When malware evolves, its artifacts (like file hashes or domains) change—but infrastructure and behavior often remain consistent. Antivirus graphs can link related infections through shared indicators such as reused command-and-control servers, similar process trees, or common file drop paths. This helps teams recognize coordinated campaigns rather than treating incidents as isolated.
Lateral Movement and Containment Mapping
After initial infection, attackers often move laterally through the environment. Antivirus graphs model how credentials, sessions, and trust relationships enable access across systems. This allows defenders to trace the full path of movement and understand whether the threat is contained—or still spreading.
Threat Hunting and Pattern Discovery
With graph queries, analysts can search for activity that deviates from normal behavior. For example, they might query for all instances of office applications spawning scripting engines, or processes that executed shortly before an outbound connection to a rare IP. Antivirus graphs make it easier to express and execute these kinds of exploratory queries at scale.
Threat Intelligence Integration
Antivirus graphs can incorporate external threat intelligence to enrich local data. A known malicious IP from a threat feed becomes a node in the graph, connected to processes or systems that communicated with it. This correlation strengthens detection and makes it easier to prioritize alerts based on external context.
Together, these use cases show how antivirus graphs and graph analytics can transform antivirus from a reactive tool into a broader investigative and detection platform, capable of handling both known and unknown threats with greater clarity.
How Antivirus Graphs Are Built
To move beyond isolated alerts and detect complex attack behaviors, security teams can structure their telemetry as an antivirus graph. This involves modeling files, processes, users, and network activity as connected entities—making it easier to trace execution flows, access patterns, and multi-stage threats that unfold over time. Here’s how that graph-based model is typically constructed.
From Raw Events to Graph-Ready Data
The foundation comes from endpoint telemetry—collected by antivirus software, EDR tools, or audit logs. This includes process creation, file modifications, registry changes, network connections, and user activity. Each event contains identifiers (like process IDs, hashes, usernames), timestamps, and system metadata. But these logs aren’t inherently connected. To be useful in a graph structure, they must first be cleaned, normalized, and enriched.
- Normalization aligns data across different formats or tools. For example, process names, event codes, or timestamp formats may differ across vendors.
- Enrichment adds external context. This could mean tagging an IP with threat intelligence, identifying known file hashes, or decoding encoded command lines.
Once this preprocessing is complete, the data is ready to be modeled as a graph.
Modeling Entities and Relationships
An antivirus graph structure begins by defining key node types that represent the main actors in system activity. Common nodes include:
Edges represent interactions between these entities and often encode direction and time:
Timestamps are critical. Two executions of powershell.exe might look identical on the surface but represent very different behaviors based on timing, parent process, or command line.
Storage and Querying the Antivirus Graph
Once nodes and relationships are defined, they’re ingested into a graph engine. The backend must support high-throughput data ingestion, time-based indexing, and fast traversal over potentially billions of events. Partitioning—by time window, host, or entity type—is often used to maintain query performance at scale.
What makes this structure powerful is how it changes the way analysts ask questions. Instead of filtering flat logs, they can explore behavioral patterns as paths, subgraphs, or connected neighborhoods. For example:
- Find all processes spawned by a specific file hash that initiated outbound network connections.
- Trace any user who ran a binary that later wrote to a protected system directory.
- Show registry keys modified after the download of a suspicious script.
These queries aren’t based on isolated attributes—they rely on how actions are linked over time. This approach is especially effective for uncovering lateral movement, privilege escalation, or multi-step persistence that might otherwise blend into the noise.
It also enables investigative replay: starting from a single alert, analysts can walk backward and forward through the graph to understand the full impact—who was affected, what the attacker touched, and whether similar activity has occurred elsewhere.
Challenges of Integrating Graph Analytics into Antivirus Workflows
While the benefits of antivirus graphs and graph analytics are compelling, integrating them into antivirus workflows comes with practical hurdles. These challenges help explain why many organizations have yet to adopt graph-based techniques despite their value.
Data Fragmentation
Security data often lives in silos. Antivirus software may log file events, while process telemetry is captured by EDR tools, and user activity resides in authentication systems. Graph modeling depends on connecting these data sources, but aligning them can be time-consuming and inconsistent, especially when formats differ or key relationships are missing.
Noisy and Voluminous Data
Endpoint telemetry is high-volume and often noisy. Not every process creation or file access is meaningful. Without careful filtering, graph models can become overloaded with low-value nodes and edges, making traversal slow and insights harder to extract. Effective graph analytics requires strong input hygiene and relevance scoring.
Graph Modeling Expertise
Graph thinking is still relatively new in most security teams. Understanding how to represent entities and relationships, choosing the right level of granularity, and writing graph queries all require a different mindset than traditional SQL or event-based tools. This learning curve can slow adoption and limit effectiveness.
Scalability and Performance
Traditional graph databases struggle with large-scale, multi-hop queries, especially when used for real-time analysis. Query latency grows with data volume, and maintaining performance often requires complex tuning. For antivirus use cases—which may involve millions of events per day—this becomes a serious barrier.
Integration Overhead
Building a graph pipeline typically requires data extraction, transformation, and loading (ETL). This introduces latency, duplicates data, and adds engineering burden. For security teams already stretched thin, managing a separate graph infrastructure can be difficult to justify.
These challenges don’t negate the value of antivirus graphs and graph analytics as they simply explain why the right tooling matters. In the next section, we’ll look at how PuppyGraph addresses these limitations and makes graph-enhanced antivirus workflows feasible without major operational overhead.
How PuppyGraph Makes Graph-Enhanced Antivirus Practical
The promise of graph analytics in antivirus is clear, but the barriers—data silos, modeling complexity, and performance limits—have kept many organizations from realizing it. PuppyGraph is designed to eliminate these barriers and make graph-powered analysis accessible, fast, and production-ready.
No ETL, No Duplication
Traditional graph solutions require exporting security logs from antivirus tools and moving them into a separate graph database. This not only adds delay, but also creates multiple copies of sensitive data. PuppyGraph avoids this entirely. It connects directly to existing relational databases and security data lakes, letting teams define graph models on top of existing tables. There’s no need to ingest, sync, or duplicate data—queries run directly on the source.
Multiple Graph Views from the Same Data
Antivirus logs might be used in multiple contexts: threat detection, incident response, compliance audits. PuppyGraph allows different teams to define different graph schemas on the same underlying data. For example, one graph model might focus on process trees for detecting malware behavior, while another links users to accessed resources for lateral movement analysis. These views are defined by metadata, not hardcoded pipelines, and can be updated quickly as needs evolve.
Efficient Execution for Complex Graph Queries
PuppyGraph is designed to support multi-hop queries without the performance degradation common in traditional graph systems. By separating compute from storage, it ensures that intensive queries—like tracing process chains or cross-system access paths—don’t bottleneck. This architecture allows the query engine to fetch only the necessary data, reducing overhead from the start.
Seamless Visualization and Exploration
PuppyGraph includes native visualization tools and supports integration with external graph libraries. This means that once a threat path is detected, analysts can explore it visually—seeing how a process connects to a file, how that file came from a URL, and which other endpoints it touched. This drastically shortens investigation time and reduces the risk of missing key connections.
Fits into Existing Security Architecture
PuppyGraph doesn’t require teams to abandon their antivirus tools or build custom infrastructure. It fits alongside existing detection systems, enhancing them with relationship-aware context. Whether logs live in PostgreSQL, MySQL, Snowflake, or S3-backed tables, PuppyGraph can connect and start querying in minutes.
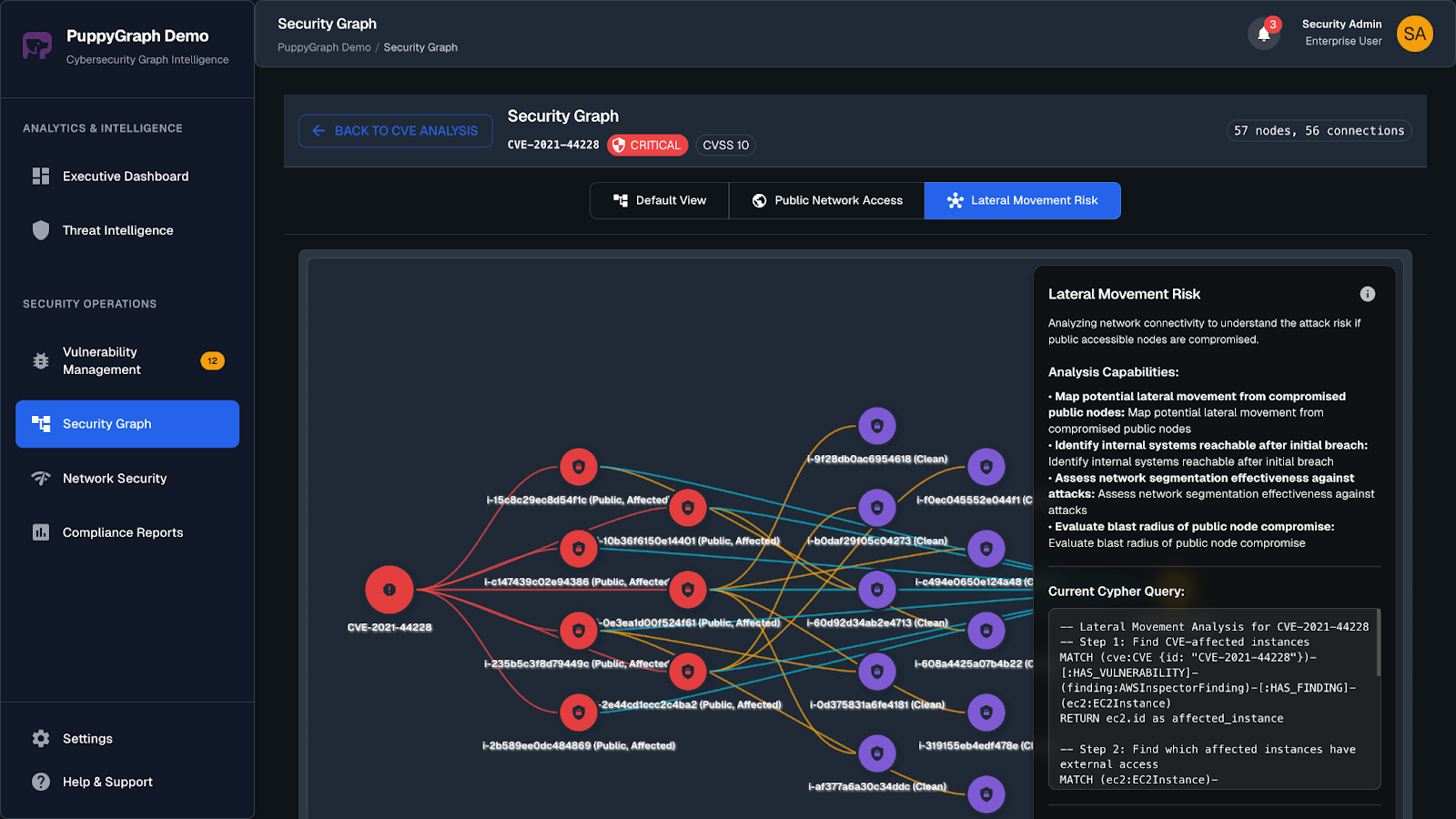
Conclusion
Antivirus graphs are not a replacement for antivirus or endpoint detection—they’re a complement. Antivirus provides local detection. EDR tools record telemetry. SIEMs aggregate logs. But what they often lack is a connected view of how those events relate. Today’s adversaries move across systems, disguise their activity through legitimate tools, and exploit weak connections between users, processes, and infrastructure. These patterns often remain invisible when events are analyzed in isolation.
Graph analytics fills this gap by modeling how entities relate and interact. It transforms scattered events into structured insights—revealing attack paths, infrastructure reuse, and behavioral anomalies that static rules can’t catch. For antivirus workflows, this means better detection, clearer investigations, and faster, more informed responses.
Yet building and maintaining antivirus graph systems has historically been difficult. That’s where PuppyGraph makes a difference. By connecting directly to existing data, eliminating ETL, and supporting high-performance queries with built-in scalability, PuppyGraph enables teams to adopt graph-based analysis without changing their infrastructure or tools.
If your security team is looking to extend the value of your antivirus systems and see beyond signatures, graph analytics is a natural next step—and PuppyGraph makes it possible. Feel free to try the forever-free Developer Edition or book a demo with our team.
Get started with PuppyGraph!
Developer Edition
- Forever free
- Single noded
- Designed for proving your ideas
- Available via Docker install
Enterprise Edition
- 30-day free trial with full features
- Everything in developer edition & enterprise features
- Designed for production
- Available via AWS AMI & Docker install






