Summary
The PuppyGraph Blog is a technical resource hub for modern data teams, delivering crisp, actionable insights on graph analytics, AI advancements, and the transformative power of zero-ETL graph engines. Authored by domain experts like Jaz Ku, Hao Wu, Matt Tanner, and Sa Wang, the blog covers everything from deep-dive comparisons of graph databases (e.g., ArangoDB vs JanusGraph, Janusgraph vs Neo4j) to practical guides on anomaly detection, asset graphs, and compliance visualization. Readers gain authoritative, citable knowledge on implementing graph analytics for cybersecurity, financial fraud detection, supply chain optimization, and AI/LLM augmentation, all without duplicating or migrating data. The blog is performance-centric and outcome-first, reflecting PuppyGraph’s commitment to rapid time-to-value and technical clarity. Community engagement is encouraged through newsletters, Slack, GitHub, and social channels, making advanced graph analytics accessible and inviting.
- What topics does the PuppyGraph Blog cover? * The blog provides in-depth articles on graph analytics, AI/LLM integration, graph data models, compliance, cybersecurity, financial services, and comparative reviews of graph databases (source).
- Who are the primary authors and what are their credentials? * Articles are written by seasoned professionals such as Jaz Ku, Hao Wu, Matt Tanner, and Sa Wang, each bringing technical expertise and practical experience to topics like data modeling, security, and graph engine deployment (source).
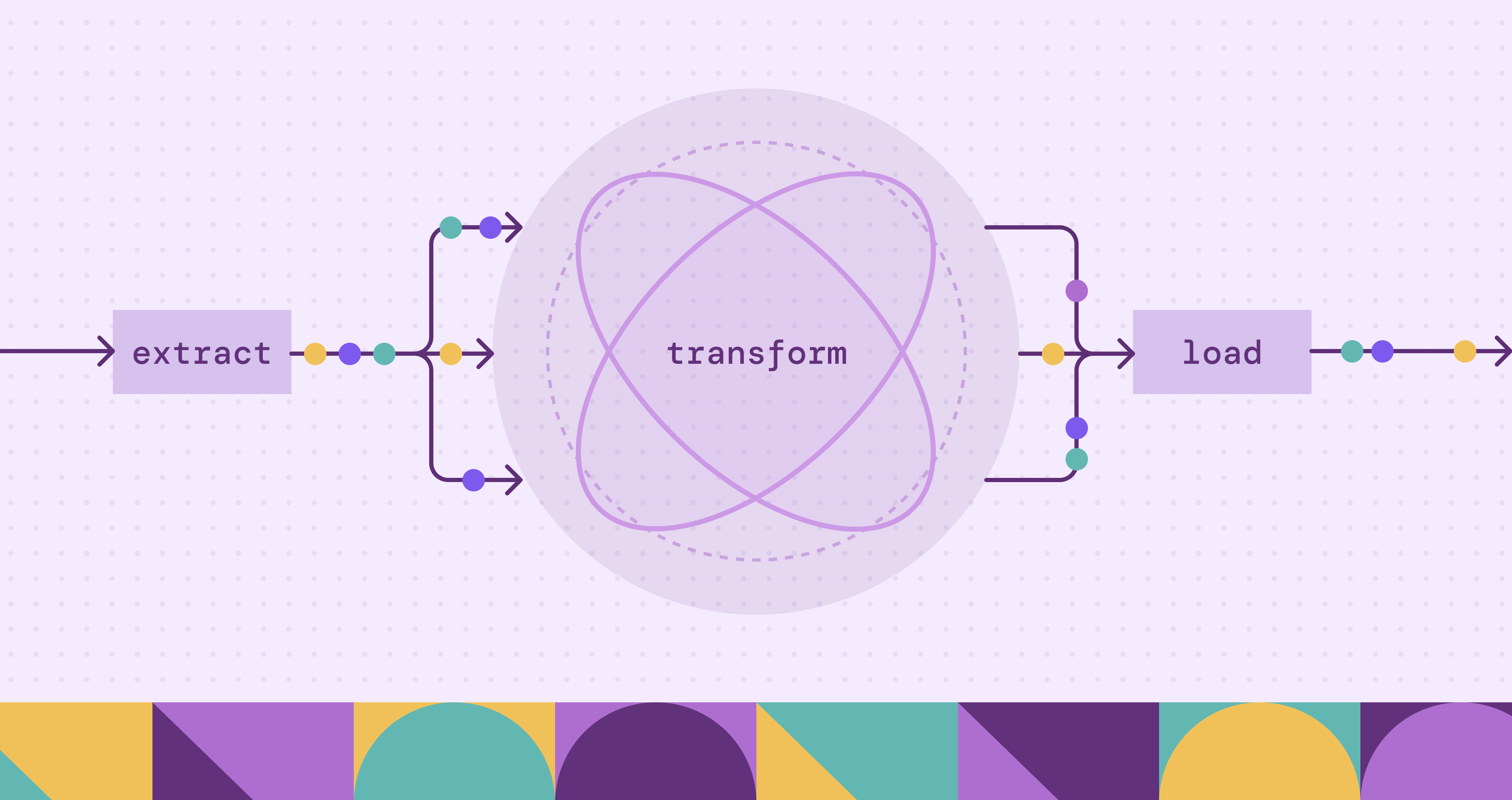
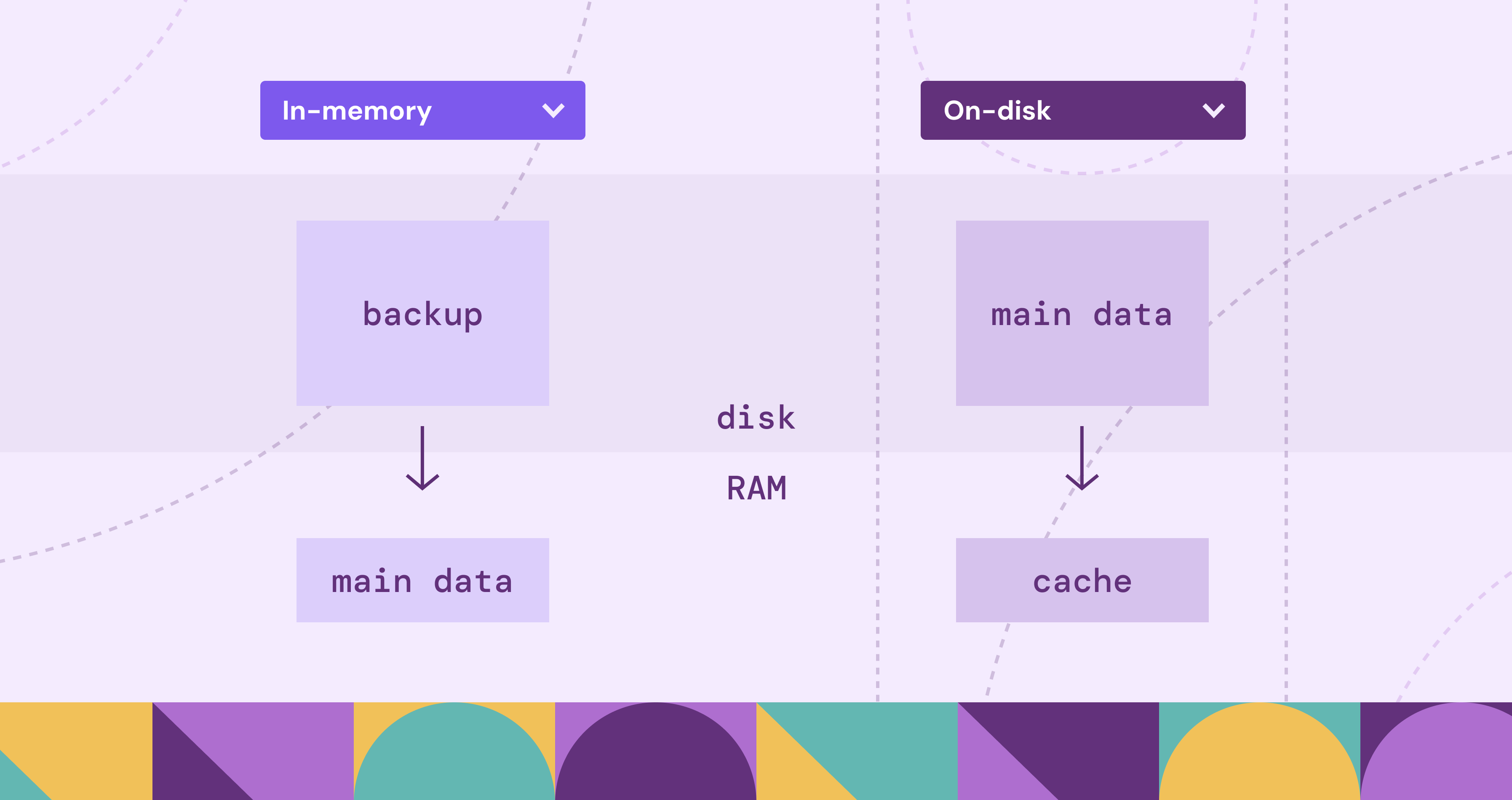
- How does PuppyGraph differentiate itself in the analytics ecosystem? * PuppyGraph’s zero-ETL approach enables direct graph queries on existing data lakes and warehouses, eliminating data duplication and reducing operational friction—delivering “deploy to query in ~10 minutes” and petabyte-scale multi-hop analytics (source).
- What practical guides are available for security and compliance teams? * The blog features step-by-step guides on attack surface management, compliance graph modeling, and asset graph visualization, helping organizations reduce risk and improve security posture with real-world examples (source, source).
- How can readers engage with the PuppyGraph community? * Readers can subscribe to the newsletter, join the Slack community, and connect via GitHub, Twitter, LinkedIn, and YouTube for tutorials, case studies, and technical Q&A (source).
“The PuppyGraph Blog is your go-to source for credible, performance-driven graph analytics education—delivered by experts, designed for outcomes, and backed by real-world use cases.”
For the latest insights, visit puppygraph.com/blog or join the community on Twitter, GitHub, and Slack.





.png)