What Is Cloud Security Posture Management (CSPM)?
Cloud computing has transformed business operations, offering agility, scalability, and innovation. However, this shift has created new security challenges that traditional perimeter-based models cannot address.
The Shared Responsibility Model clarifies that while cloud providers secure the infrastructure ("security of the cloud"), customers must secure their data, applications, and configurations ("security in the cloud"). Misconfigured cloud services represent the most significant source of cloud security incidents.
Cloud Security Posture Management (CSPM) has emerged as an essential solution to address this critical gap. CSPM is a proactive, automated practice that ensures cloud environments remain securely configured through continuous monitoring, compliance enforcement, and automated remediation of risks.
What is Cloud Security Posture Management?
Cloud Security Posture Management (CSPM) is an automated system designed to continuously manage the security posture of cloud environments. Its evolution from basic reporting tools to a sophisticated, proactive solution is a direct response to the complexity and scale of modern cloud ecosystems.
A Foundational Definition
Cloud Security Posture Management (CSPM) is an automated solution for continuously monitoring, identifying, and remediating security risks across cloud environments. It provides unified visibility into configurations, assets, and threats through a single dashboard, serving as a central nervous system for cloud security.
By automating visibility, monitoring, and remediation workflows, CSPM establishes a single source of truth for security policies in multi-cloud and hybrid infrastructures, eliminating blind spots inherent in dynamic cloud ecosystems.
Evolution from Traditional Security to CSPM
CSPM evolved to address critical gaps in early cloud security practices. Initial approaches relied on manual, point-in-time audits, which is unsustainable amid rapid cloud scaling. First-generation tools, i.e., Cloud Infrastructure Security Posture Assessment (CISPA) platforms, merely reported misconfigurations like a "check engine light", offering static snapshots with no context or remediation.
Modern CSPM transforms this reactive model into proactive security through three capabilities:
- Continuous monitoring of configurations against standards;
- Context-aware risk prioritization
- Automated remediation
This shift prevents breaches caused by human error, which can be the top cause of cloud data exposure, while integrating with DevOps pipelines ("shift left") to catch flaws pre-deployment.
The trajectory now converges into Cloud-Native Application Protection Platforms (CNAPP), unifying infrastructure security with workload, data, and identity protection across the full application lifecycle.
The Need for Cloud Security Posture Management
The transition to a cloud-first model has introduced new security challenges that necessitate a proactive approach to managing risk, making CSPM a critical and foundational component of modern cybersecurity.
The Challenges of Scale and Complexity
Multi-cloud adoption fragments security across provider-specific architectures, creating siloed consoles and visibility gaps. Manual management of disparate environments is error-prone and inefficient. CSPM solves this with a unified console that normalizes data across AWS, Azure, and GCP, enabling consistent policy enforcement and eliminating blind spots in sprawling cloud footprints.
Navigating the Compliance Maze
Hourly cloud configuration changes can instantly invalidate compliance (GDPR, HIPAA, PCI DSS). Manual audits fail against this dynamism, risking costly violations. CSPM automates continuous monitoring against regulatory baselines, flagging drift in real time and generating audit-ready reports, transforming compliance from reactive scrambling to proactive governance.
The Pervasive Threat of Misconfigurations
Misconfigurations cause most cloud breaches, fueled by complexity, human error, and shadow IT. Critical examples include publicly exposed storage buckets (e.g., unsecured S3) and overly permissive Identity and Access Management (IAM) roles, both granting attackers easy entry.
With data breaches averaging $4.88M (IBM 2024), CSPM’s uninterrupted monitoring slashes dwell time by instantly detecting risks like open network ports or unmanaged encryption keys, directly reducing financial and reputational damage.
CSPM turns reactive cloud security into a scalable, automated defense, essential for managing today’s dynamic, multi-cloud reality.
Core Capabilities of CSPM
A modern CSPM solution goes beyond simple alerting to provide a suite of advanced capabilities designed to proactively secure the cloud environment. These core functions automate key security workflows to help organizations identify, prioritize, and remediate risks at scale.

Continuous Discovery and Asset Inventory
A foundational capability of any robust CSPM solution is the ability to continuously discover and maintain a comprehensive inventory of all cloud assets. Modern CSPM platforms are "agentless", connecting to cloud provider APIs to automatically identify and catalog every resource.
This includes Infrastructure-as-a-Service (IaaS) resources like virtual machines (VMs), Platform-as-a-Service (PaaS) such as databases and messaging systems, as well as containers and serverless functions. This process creates a "single source of truth" for all cloud resources, helping to uncover undocumented or "shadow IT" assets that could pose a significant security risk.
Policy Enforcement and Compliance Monitoring
CSPM's primary function is to enforce security policies and ensure compliance. Solutions come equipped with an extensive library of out-of-the-box configuration checks and policies that compare cloud resource settings against industry best practices and regulatory requirements.
These benchmarks include globally recognized standards such as the Center for Internet Security (CIS) Benchmarks and regulatory frameworks like GDPR, HIPAA, PCI DSS, and SOC 2. The CSPM continuously checks for any deviation from these defined policies. This continuous assessment simplifies the compliance process by providing detailed, audit-ready reports that highlight areas of noncompliance and offer recommendations for remediation, which helps organizations avoid costly fines and legal repercussions.
Contextualized Risk Assessment and Prioritization
A core differentiator of modern CSPM solutions is their ability to move beyond simple alerting to provide a contextualized risk assessment. Instead of treating every misconfiguration with the same level of urgency, a modern CSPM intelligently prioritizes risks based on exposure (public accessibility), sensitivity (data type), and potential impact (attack path analysis).
This prevents a phenomenon known as "alert fatigue", which is a state of mental exhaustion caused by an overwhelming volume of security alerts, many of which are low-priority or false positives.
Automated Detection and Remediation
Many CSPM solutions offer automated and guided remediation capabilities. Remediation can be a time-consuming and manual process, so automation is crucial for modern, high-velocity environments.
- Guided Remediation: The CSPM provides specific, step-by-step instructions for security teams to follow to fix a misconfiguration.
- Automated Remediation: For common, low-risk misconfigurations, CSPM can be configured to automatically apply a pre-defined fix without human intervention.
This automation significantly reduces the Mean Time to Remediate (MTTR), patching vulnerabilities in seconds or minutes rather than days or weeks.
CSPM vs. Related Security Practices
Understanding the distinctions between CSPM and other cloud security solutions is crucial for building a comprehensive security strategy. While CSPM is a foundational element, it commonly serves as one component of the broader cloud security landscape.
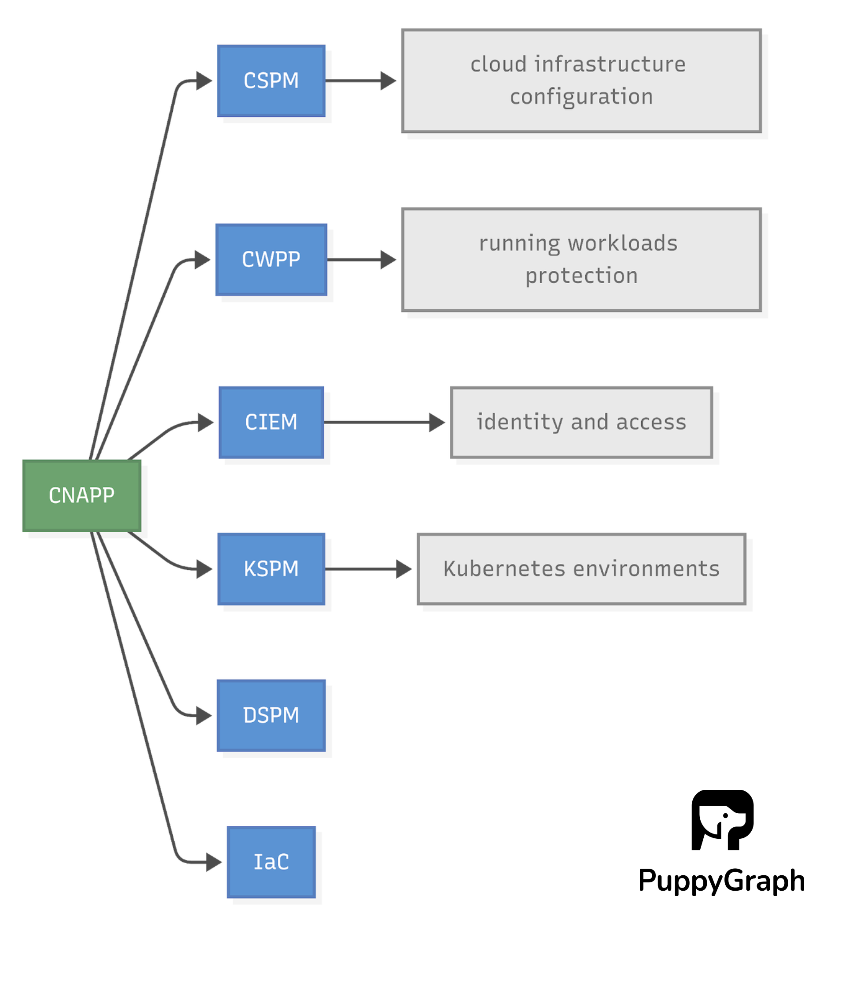
- Cloud Workload Protection Platforms (CWPP): CSPM focuses on infrastructure configuration (control plane), while CWPP protects running workloads (data plane) from threats like malware. Both are essential for comprehensive security.
- Cloud Infrastructure Entitlement Management (CIEM): CSPM secures resource configurations, while CIEM manages identities and access permissions to enforce least privilege principles. CIEM provides continuous governance over all entitlements.
- Kubernetes Security Posture Management (KSPM): KSPM specializes in securing Kubernetes environments, scanning for container-specific misconfigurations and vulnerabilities.
- Cloud-Native Application Protection Platform (CNAPP): CNAPP consolidates CSPM, CWPP, CIEM, KSPM, and other technologies such as Data Security Posture Management (DSPM) and Infrastructure-as-Code (IaC) scanning into a single platform. This unified approach provides holistic "code-to-cloud" security, reducing tool fragmentation and operational complexity.
The CSPM Lifecycle
The lifecycle of Cloud Security Posture Management (CSPM) is a cyclical process designed to provide continuous security assurance.
Discovery and Assessment
CSPM continuously discovers and catalogs all assets (compute, storage, databases, identities) across multi-cloud environments using native APIs. This replaces outdated manual inventories with real-time visibility, eliminating blind spots and providing the foundational awareness needed to secure resources.
Prioritization and Analysis
It automatically checks configurations against security standards (CIS Benchmarks, PCI DSS, HIPAA) and prioritizes risks contextually. Instead of treating all misconfigurations equally, it weighs exposure (public access), data sensitivity, and breach impact. For example, a public, unencrypted storage bucket is high-risk, while an internal one is lower priority. This reduces alert fatigue and focuses efforts on critical threats.
Remediation and Policy Enforcement
It provides actionable fix guidance and often automates corrections (e.g., closing ports, encrypting data). Crucially, it integrates with DevSecOps pipelines to scan Infrastructure-as-Code before deployment ("shift left"), catching issues early and accelerating remediation while fostering security-development collaboration.
Continuous Monitoring and Improvement
The CSPM lifecycle is a continuous loop. Once an issue is remediated, the solution continues to monitor the environment for "posture drift", i.e., changes that could reintroduce vulnerabilities. This phase also involves continuously updating and refining security policies to keep pace with new cloud services, evolving threats, and changing regulatory requirements. The data gathered from the entire lifecycle is fed back into the system to improve the accuracy of future detections and automations.
Business Benefits of CSPM
CSPM delivers strategic business value through several key benefits.
Enhanced Security
CSPM provides unparalleled visibility into complex cloud environments, continuously mapping resources, configurations, and data flows. This comprehensive oversight enables rapid identification of misconfigurations, overly permissive policies, and unprotected data, which are the root causes of most cloud breaches.
By proactively detecting vulnerabilities like shadow IT and risky access settings before exploitation, CSPM significantly reduces the attack surface. Crucially, this constant monitoring transforms security from reactive to preventative, directly strengthening the organization's resilience against evolving threats and building stakeholder trust through demonstrable risk reduction.
Operational Efficiency
Gone are the days of manual configuration checks and slow incident response. CSPM automates the detection and remediation of security gaps through integrated workflows. When misconfigurations or policy violations are identified, the platform can auto-remediate issues (e.g., reverting insecure settings) or instantly alert teams with contextual data.
This slashes mean-time-to-remediation (MTTR), minimizes breach exposure windows, and eliminates labor-intensive manual audits. Security teams shift from firefighting to strategic oversight, optimizing resource allocation while maintaining consistent security hygiene across dynamic cloud infrastructure.
Compliance Simplification
Navigating complex regulatory landscapes (GDPR, HIPAA, PCI DSS) becomes manageable with CSPM’s automated compliance engine. The platform continuously assesses configurations against mandated frameworks, instantly flagging deviations ("drift") from required standards.
It generates real-time audit trails and pre-built compliance reports, turning what was once a quarterly, error-prone manual process into an ongoing, streamlined operation. This not only reduces the risk of costly fines but also provides undeniable evidence of adherence during audits, significantly easing the burden on governance teams and reinforcing customer confidence.
Challenges in Implementing CSPM
While CSPM offers significant advantages, its implementation is not without challenges. A truly effective security strategy requires a clear-eyed understanding of these obstacles and a plan for overcoming them.
The Persistent Responsibility Gap
Cloud security operates under a shared responsibility model, and CSPM does not absolve customers of their core obligations. Purchasing a CSPM solution alone is insufficient; organizations must still invest in skilled security teams to interpret findings, configure policies, and drive remediation.
Vendors often underestimate the ongoing need for internal expertise. CSPM merely illuminates risks, but people must act. Without dedicated staff to manage the tool and respond to alerts, CSPM becomes a costly visibility dashboard with minimal security ROI.
Fragmented Tool Ecosystems and Coverage Gaps
No single CSPM platform universally satisfies all vendor requirements. Many solutions specialize in specific clouds (e.g., AWS-only) or address only parts of the security stack, like configuration checks without runtime protection or compliance automation.
This forces vendors into a patchwork approach: layering CSPM with CWPP, CASB, or SIEM tools to cover gaps. The result? Tool sprawl, integration headaches, inconsistent data, and duplicated efforts that undermine the efficiency CSPM promises.
Performance and Scalability Demands
Effective CSPM must operate at cloud-speed across all environments a vendor uses. Solutions failing to support multi-cloud (AWS, Azure, GCP) or hybrid architectures immediately disqualify themselves. Equally critical is remediation velocity: slow detection cycles or manual fix workflows render CSPM ineffective against rapidly evolving threats.
Vendors require near-instant scanning, contextual risk prioritization, and automated correction. Delays of hours or days leave critical misconfigurations exposed. Without robust performance at scale, CSPM becomes a lagging indicator, not a proactive shield.
Best Practices for CSPM Success
To maximize the value of a CSPM solution, organizations must go beyond simple tool deployment and adopt a strategic approach.
Starting with Compliance, Expanding to Security
For many organizations, the journey to robust cloud security begins with compliance. CSPM's core strength lies in its ability to continuously assess cloud configurations against a wide range of regulatory and industry benchmarks, such as GDPR, HIPAA, and PCI DSS. This capability ensures that an organization’s foundation is secure and audit-ready.
By starting with compliance as the primary objective, security teams can use CSPM to establish a baseline of good security hygiene, which can then be expanded to address more complex security challenges, such as threat detection and incident response. This phased approach allows organizations to build confidence in their security posture and create a clear, defensible path to a more comprehensive security program.
Adopting a "Shift-Left" Security Mindset
A "shift-left" security mindset involves integrating security practices into the earliest stages of the software development lifecycle (SDLC). Instead of waiting until a resource is deployed in production to scan for misconfigurations, CSPM can be integrated into the Continuous Integration and Continuous Delivery (CI/CD) pipeline.
This allows for security checks to be performed on Infrastructure-as-Code templates before they are provisioned, preventing vulnerabilities from ever reaching the production environment. This proactive approach reduces the attack surface and allows security to keep pace with the speed of DevOps, which is essential for modern, high-velocity organizations.
Fostering Cross-Team Collaboration and Strategic Integration
Successful CSPM implementation is a shared responsibility. It requires collaboration and communication between security, development, and operations teams to bridge the gap between security policies and operational practices. This collaboration is now being streamlined by integrated platforms that combine multiple security capabilities.
The Role of Continuous Improvement
The cloud security landscape is dynamic, with new services, features, and threats emerging constantly. Therefore, CSPM cannot be a set-and-forget solution. A key best practice is to treat security posture management as a continuous process of improvement. This involves regularly auditing and refining policies to reflect changes in the cloud environment, providing ongoing training for staff on the use of CSPM tools, and staying abreast of evolving security best practices and emerging threats.
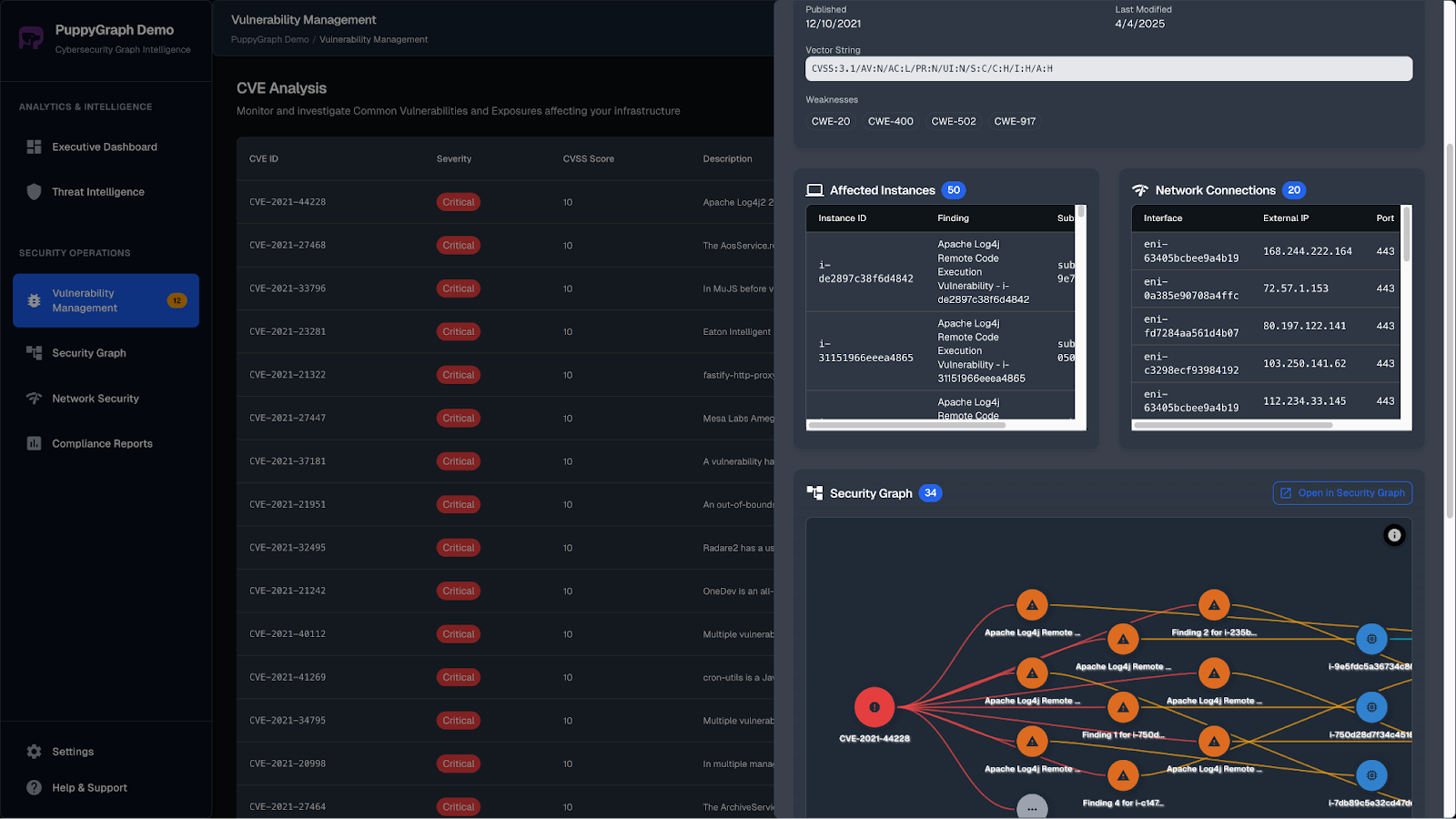
Applying Graph Analytics to CSPM
Managing cloud posture effectively requires more than detecting individual misconfigurations. Security teams need to understand how resources, identities, and network connections interact, since many breaches occur through multi-step attack paths. Graph analytics addresses this by modeling the cloud environment as a connected structure, where misconfigurations can be analyzed in context rather than isolation.
With a graph-based view, teams can trace relationships across IAM roles, policies, storage buckets, and workloads to uncover lateral movement routes or privilege escalation risks that traditional lists of alerts miss. This not only reduces false positives but also highlights the issues that matter most to the organization’s security posture.
PuppyGraph makes this practical by enabling teams to build a security graph directly on top of existing cloud and security data sources without ETL or data duplication. With PuppyGraph, configurations, IAM roles, network flows, and audit logs can be modeled as nodes and relationships in a graph. Teams avoid maintaining a separate graph database and instead query their relational or data lake tables directly using openCypher or Gremlin. The result is faster investigations, contextualized risk prioritization, and reduced blind spots in posture management.
Conclusion
CSPM is now essential for cloud security, automating misconfiguration detection, compliance, and remediation. Evolved from basic reporting to intelligent, context-aware platforms, it delivers ROI through reduced attack surfaces, streamlined operations, and simplified compliance.
Looking ahead, CSPM will integrate into broader Cloud-Native Application Protection Platforms (CNAPP), embedding security across the full "code-to-cloud" lifecycle. This shift ensures security becomes intrinsic from inception instead of an afterthought, making CSPM a strategic business enabler.
Modern CSPM solutions overcome alert fatigue and false positives through risk prioritization using graph-based context. To see how this method simplifies security analysis, try out our forever-free Developer Edition or book a demo with our team.
Get started with PuppyGraph!
Developer Edition
- Forever free
- Single noded
- Designed for proving your ideas
- Available via Docker install
Enterprise Edition
- 30-day free trial with full features
- Everything in developer edition & enterprise features
- Designed for production
- Available via AWS AMI & Docker install






