What is Application Security Posture Management (ASPM)?
The modern software development environment is defined by unprecedented speed and complexity. Enterprises have adopted rapid development cycles, agile methodologies, and cloud-native architectures that rely on microservices, APIs, and extensive use of open-source components. While this has accelerated innovation, it has also introduced a significant security challenge: a massive increase in the attack surface and an explosion of potential vulnerabilities.
This rapid pace has created a critical gap between the speed of development and traditional security models. Legacy Application Security (AppSec) models, which often involve periodic, siloed security assessments, are no longer sufficient. Organizations are drowning in a flood of security alerts from a multitude of disparate tools, leading to "alert fatigue" where security teams are overwhelmed. This operational bottleneck is a direct path to accumulating security debt and can even break down the very DevSecOps principles intended to unite development and security teams.
In response, Application Security Posture Management (ASPM) has emerged as a new strategic approach. ASPM is designed to address the fragmented and reactive nature of traditional AppSec by providing a single, consolidated view of an organization's application security landscape, thereby transforming risk management into an automated, data-driven process.
What is Application Security Posture Management?
Application Security Posture Management is a unified and holistic security approach that continuously discovers, assesses, prioritizes, and remediates risks across the entire software development lifecycle (SDLC). It serves as a single source of truth for an organization's AppSec program by aggregating and correlating security findings from a variety of sources into one unified dashboard. Compared with cloud security posture management (CSPM), ASPM focuses on the application layer, while CSPM secures cloud infrastructure.
Gartner describes ASPM as an approach that assesses "security signals" across the three key phases of the SDLC: design, development, and runtime. These help enhance visibility, enforce security policies, and ultimately, strengthen an organization's overall security posture. ASPM is not merely a tool, but a strategic approach and a set of technologies designed to provide continuous assessment and improvement of an application's security posture throughout its entire lifecycle. The core value of ASPM is not in generating new security findings, but in providing the intelligence and context to make sense of the findings that already exist.
The Need for Application Security Posture Management
The need for ASPM is a direct consequence of the systemic challenges created by the shift to modern, agile software development.
The Acceleration of Development Cycles
The shift to agile methodologies and Continuous Integration and Continuous Delivery (CI/CD) pipelines has dramatically increased deployment velocity. While this enables rapid innovation, it also compresses the window for security validation. Traditional, manual, or siloed AppSec processes simply cannot scale to match the pace of modern development, increasing the likelihood that exploitable vulnerabilities are introduced into production unnoticed.
Alert Fatigue and Tool Sprawl
Security teams are inundated with thousands of vulnerability alerts from disparate tools, many of which are low-severity, duplicates, or false positives. Without intelligent correlation and contextual prioritization, teams suffer from alert fatigue, leading to critical risks being deprioritized or missed entirely.
Fragmented Architectures Create Visibility Gaps
Modern application architectures, such as microservices, containers, and serverless functions, present another significant challenge. These environments consist of a large number of ephemeral components and "moving parts", making it difficult to gain continuous visibility and track risks. This architectural complexity creates a visibility gap that traditional tools cannot bridge.
ASPM provides the necessary full-stack visibility, mapping every service, API, dependency, and data flow to eliminate these blind spots and provide a comprehensive view of the application landscape.
Core Capabilities of ASPM
Modern ASPM solutions are designed to combine, consolidate, and automate application security processes.
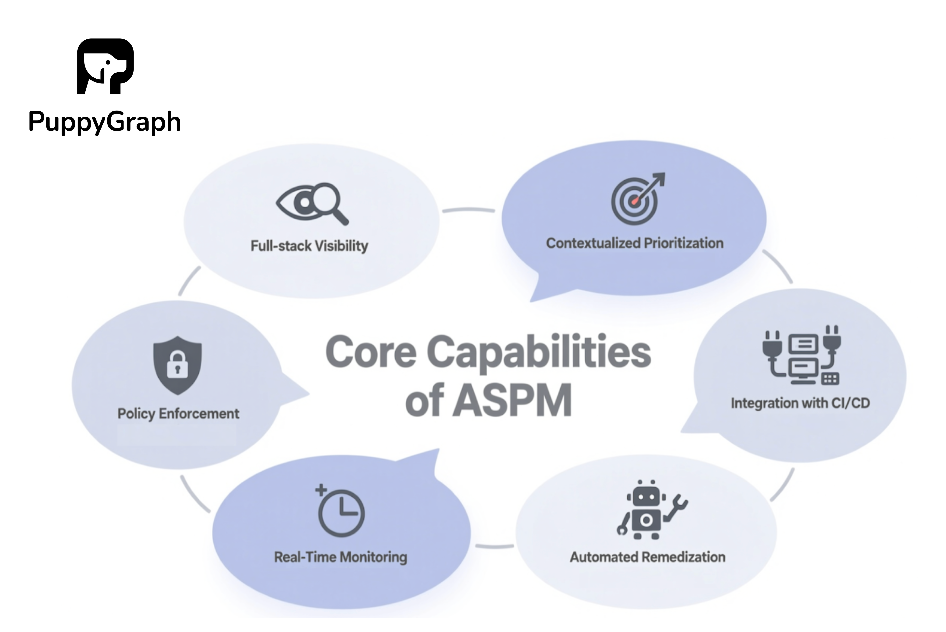
Full-Stack Visibility
ASPM solutions provide comprehensive visibility across the entire application stack, from code to the underlying cloud infrastructure. This holistic view connects the dots between code, cloud workloads, and runtime environments, ensuring there are no security blind spots.
Contextualized and Risk-Based Prioritization
ASPM's core function is to move beyond simply identifying vulnerabilities to prioritizing the ones that matter most. It correlates findings from multiple sources and applies business context to determine which issues pose the greatest threat, enabling teams to focus on the most critical vulnerabilities.
Automated Policy Enforcement
ASPM empowers organizations to centrally define, enforce, and monitor security policies across their entire software development footprint. By automating policy checks within the CI/CD pipeline, ASPM ensures that security standards are consistently applied and that the risk of human error is reduced.
Seamless Integration with CI/CD and Developer Workflows
A key differentiator of ASPM is its deep integration with CI/CD pipelines, source code repositories, and developer tools. This enables a "shift-left" security strategy where security checks are run early in the software development process, when fixing vulnerabilities is significantly more cost-effective.
Real-Time Monitoring and Continuous Assessment
ASPM continuously monitors applications in real-time, allowing for the identification of new issues as they arise. This proactive approach ensures that the security posture of an application evolves alongside its development and deployment.
Automated Threat Detection and Remediation Guidance
ASPM leverages intelligent automation to detect threats and provide actionable remediation guidance. The platform can automatically generate tickets and assign them to the correct code owners, which significantly reduces the mean time to repair (MTTR).
ASPM vs. Traditional AppSec Tools
ASPM platforms are not standalone security testing tools, but rather "data aggregators" that unify the output of other tools. An ASPM solution serves as a central management layer for an organization's AppSec program. Its primary function is to aggregate, analyze, and prioritize security findings from a wide array of sources into a single, unified view of risk. A key limitation is that an ASPM platform does not perform security testing on its own; its effectiveness is entirely dependent on the quality of the data it receives from the tools it integrates with.
ASPM and traditional security tools are best viewed as complementary components of a comprehensive security strategy. ASPM acts as the brain that takes the output from the "eyes and ears", the SAST, DAST, and SCA tools, and translates it into actionable intelligence for an organization.
The ASPM Lifecycle
The ASPM lifecycle is a continuous, closed-loop process that automates the transition from raw security data to actionable business intelligence.
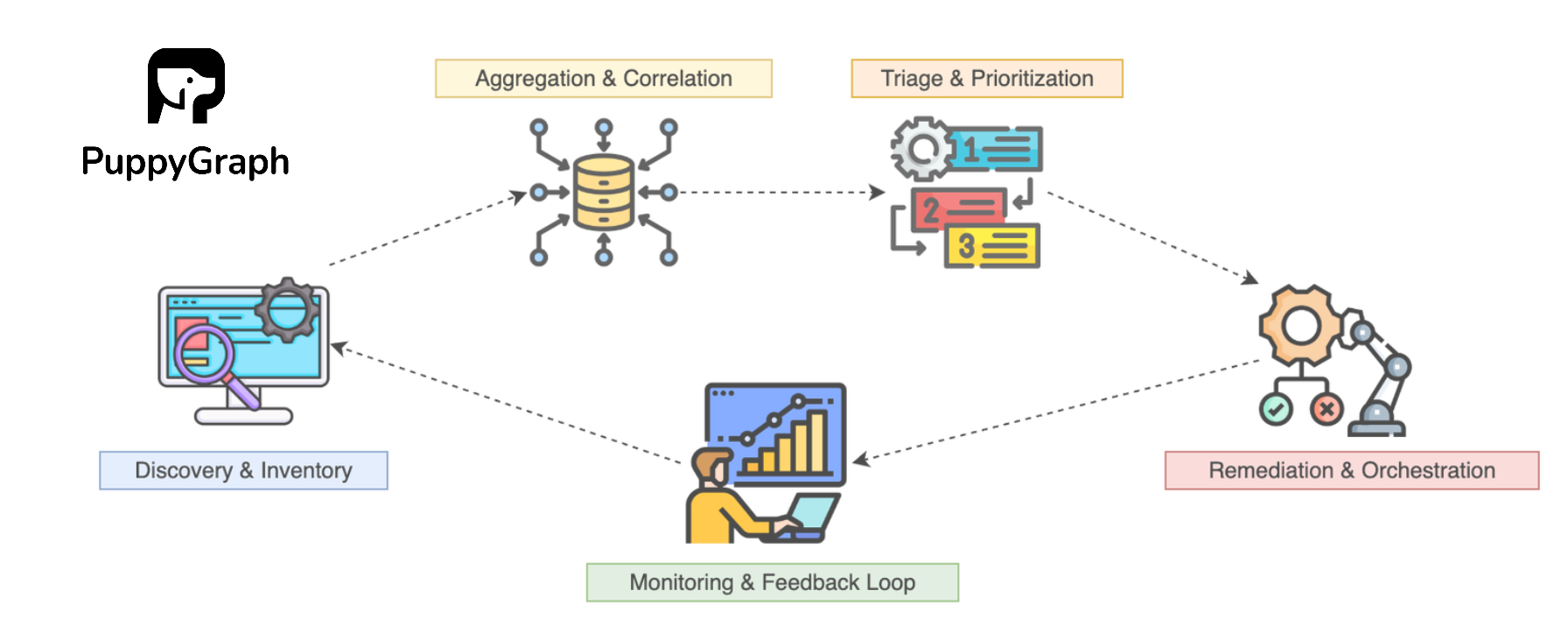
- Discovery and Inventory: The lifecycle begins with a continuous assessment of all applications and their components, including custom code, open-source libraries, and APIs. This is crucial for identifying "shadow IT" and maintaining a real-time inventory of assets.
- Aggregation and Correlation: ASPM platforms ingest findings from various tools, correlating and unifying the data into a single source of truth. This deduplicates redundant alerts and brings order to fragmented security data.
- Triage and Prioritization: The platform triages and prioritizes findings based on a risk-based scoring model that considers business impact, exploitability, and proximity to sensitive data. This separates signal from noise and helps teams focus on the highest-risk issues.
- Remediation and Orchestration: ASPM automates the remediation workflow by providing actionable guidance and automatically generating and assigning tickets to the correct code owners. This reduces delay and transforms a technical finding into a streamlined business process.
- Monitoring and Feedback Loop: The final phase involves continuous monitoring to track security posture over time. The platform analyzes the outcomes of security actions and refines the posture, providing clear metrics to demonstrate progress to stakeholders.
Business Benefits of ASPM
Implementing an ASPM solution provides significant business value that influences an organization's financial standing, risk profile, and operational efficiency.
Enhanced Risk Management and Data-Driven Decision-Making
ASPM provides a comprehensive, real-time view of the application security landscape, empowering executives with the insights needed to make informed, data-driven decisions. By enabling leaders to quantify and visualize security risks in business terms, ASPM helps justify security expenditures and demonstrate a clear return on investment to board members and stakeholders. This elevated level of visibility into business context allows for the effective allocation of security resources to the areas that matter most.
Operational Efficiency and Cost Reduction
ASPM automates many aspects of security management, from vulnerability triage to remediation, which leads to significant operational efficiencies and cost savings. By reducing the manual effort required for security assessments, vulnerability management, and compliance reporting, ASPM frees up valuable resources. The platform acts as a "force multiplier" for security teams, enabling a small team to handle a much larger volume of findings without needing to scale staff. Furthermore, by enabling a "shift-left" security strategy, ASPM helps catch vulnerabilities earlier, which "dramatically" reduces the cost of remediation compared to addressing them in production.
Accelerated Rollouts and Application Resilience
By automating security processes and providing continuous, real-time monitoring, ASPM ensures that applications remain resilient against emerging threats. It enables organizations to build and maintain secure, high-quality applications that can withstand evolving cyberthreats, thereby minimizing the risk of breaches or system failures and supporting digital transformation initiatives. This security-first approach allows executives to confidently drive innovation and new product rollouts without compromising security.
Strengthened Compliance and Audit Readiness
ASPM helps organizations maintain compliance with a wide range of industry regulations and security frameworks, such as GDPR, HIPAA, and PCI DSS. The platform's continuous monitoring and detailed reporting capabilities provide comprehensive audit trails, which significantly reduces the burden of manual audits and ensures that applications remain compliant over time.
Challenges in ASPM Implementation
While ASPM offers a powerful solution, its successful implementation is not without hurdles.
Integration Friction with Legacy Frameworks
Some ASPM’s holistic risk-context approach can clash with siloed AppSec programs built around point tools (SAST, DAST, SCA). Organizations may struggle to retrofit ASPM into existing workflows, leading to manual data stitching between disconnected systems. Re-engineering processes to prioritize application-specific risks across development and production requires significant effort, and risks creating tool sprawl instead of consolidation.
Cloud Environment Compatibility
ASPM tools must natively support hybrid/multi-cloud architectures while ingesting data from CSPM, CNAPP, and cloud-native services (Kubernetes, serverless). Solutions failing to correlate runtime behavior with IaC configurations or cloud posture leave critical blind spots. Without seamless API integration across AWS, Azure, and GCP environments, ASPM cannot deliver the unified visibility needed to map attack paths across infrastructure layers.
DevOps Pipeline Integration
Embedding ASPM into CI/CD workflows demands frictionless adoption. Scans must complete within minutes not hours, to avoid disrupting release velocity. Tools that lack native integrations with Jenkins, GitHub Actions, or GitLab slow development cycles with complex approvals or false positives. Successful implementation requires automated pull request remediation, pipeline gating, and developer-friendly fix guidance without compromising deployment speed.
Solution Selection in a Nascent Market
As a nascent category, ASPM solutions vary wildly: some emphasize AI-driven exploit prediction, others focus on business-impact scoring or open-source vulnerability mapping. Organizations without clearly defined needs risk selecting tools overloaded with irrelevant features.
Best Practices for ASPM
Successful ASPM implementation requires a strategic approach that addresses both technical and organizational dimensions.
Foster a Culture of Shared Responsibility
The ultimate success of an AppSec program relies on its people. Organizations should invest in continuous security training for developers to help them understand the security implications of their code and adopt secure coding practices.This proactive approach reduces the number of vulnerabilities introduced at the source, thereby easing the burden on security teams in later stages of the SDLC. Bridging the historical friction between security and development teams and establishing a shared responsibility is crucial for effective implementation.
Establish a Robust Governance Framework
Organizations should begin by establishing a clear governance framework that defines security responsibilities across development, operations, and security teams. This includes creating standardized security policies, defining acceptable risk thresholds, and establishing clear escalation procedures for critical vulnerabilities. This proactive step helps to break down silos and ensures that security is a shared responsibility rather than a separate checkpoint.
Develop a Strategic Integration Plan
A successful ASPM deployment is not a simple plug-and-play solution. Organizations should prioritize ASPM solutions that integrate seamlessly with their existing development toolchains, including source code repositories, CI/CD pipelines, and project management systems. This strategic integration is fundamental to embedding security into the development process and ensuring the ASPM platform receives the rich, contextual data it needs to function effectively.
Adopt a Risk-Based Prioritization Model
Instead of trying to address every single vulnerability, which is often impossible and inefficient, remediation efforts should concentrate on the issues that present the greatest risk to business operations. This approach involves assessing vulnerabilities based on their exploitability, business impact, and exposure levels, enabling effective and practical allocation of security resources. This shifts the focus from an unattainable "zero vulnerabilities" mindset to a practical, business-aligned approach.
Apply Graph Analytics for Risk Context
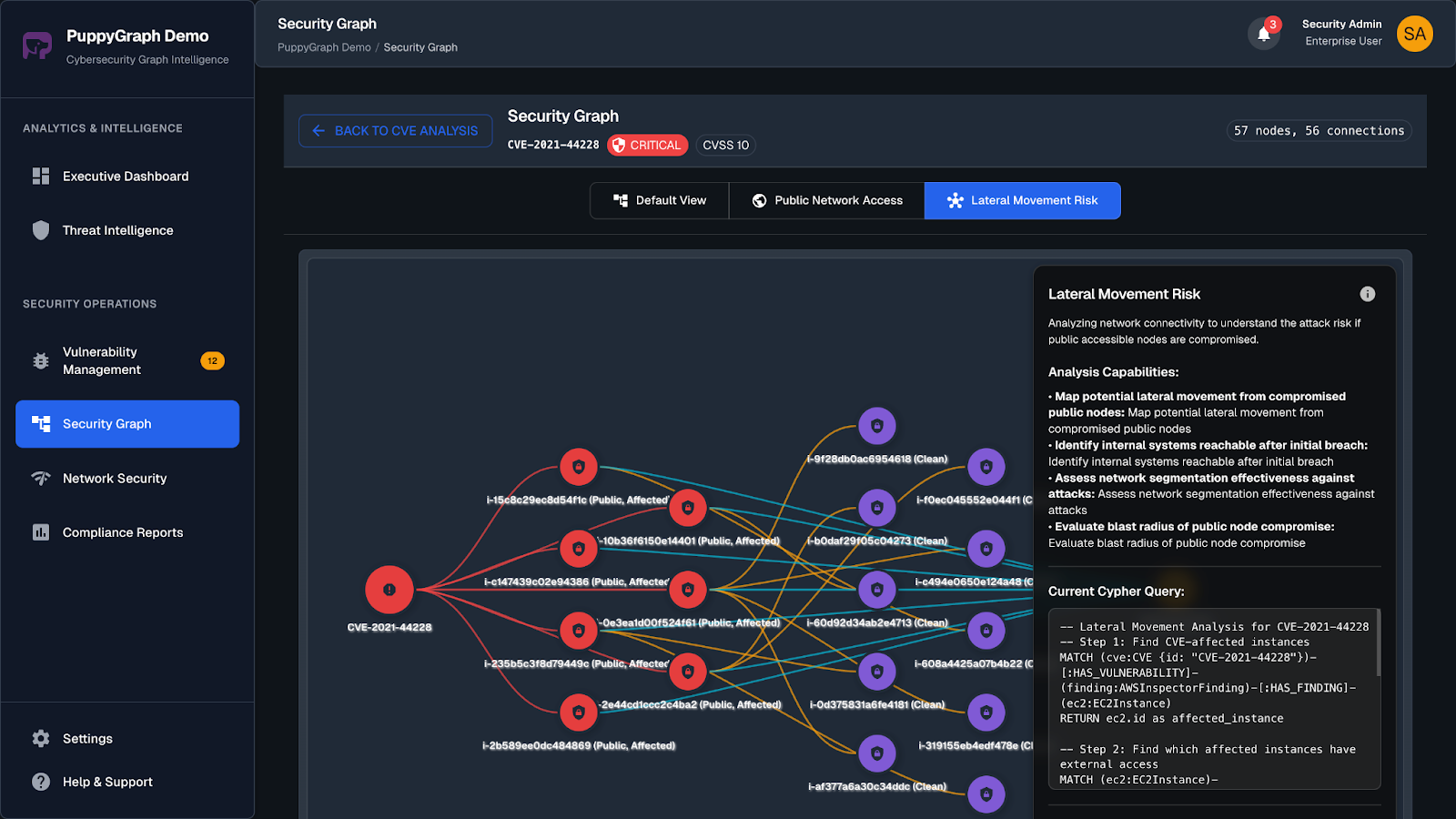
Applications rarely exist in isolation. They are built from services, APIs, third-party libraries, and infrastructure components that interact in complex ways. Vulnerabilities in one part of the system often create indirect risks elsewhere, such as privilege escalation through a chain of services or exposure through a shared dependency. Understanding these multi-hop relationships is difficult with traditional lists or dashboards, but this is where graph modeling strengthens ASPM. By representing applications, components, and vulnerabilities as nodes and their relationships as edges, security teams can trace how risks propagate through the environment.
PuppyGraph makes this approach practical without requiring new infrastructure. As a zero-ETL graph query engine, it connects directly to your existing application data sources, such as vulnerability scanners, CI/CD pipelines, or software composition analysis results, and queries them as a unified graph. This eliminates the need to duplicate or migrate data into a graph database.
With PuppyGraph, teams can create multiple graph views over the same datasets, such as one centered on attack path analysis and another on dependency risk. Queries written in openCypher or Gremlin uncover hidden connections in seconds, even across large, rapidly changing environments. This capability transforms ASPM from merely listing vulnerabilities to prioritizing them in context, identifying the few issues that create real attack paths instead of overwhelming users with alerts.
Conclusion
ASPM represents a critical evolution in application security, moving from a fragmented, reactive approach to a unified, proactive, and data-driven strategy. It is the necessary solution to the systemic challenges posed by modern software development, providing the visibility and control required to manage increasingly complex and dynamic application environments. By serving as a single source of truth, ASPM brings order to the chaos of tool sprawl and alert fatigue, enabling security and development teams to collaborate effectively and focus on the most critical risks.
Looking ahead, ASPM is poised for even greater advancement with a growing reliance on AI and machine learning for predictive threat detection, root cause analysis, and proactive risk scoring. Ultimately, ASPM is not just a technology platform; it is a strategic investment that transforms the economics of application security, providing a measurable return on investment in the form of reduced breach risk, accelerated compliance, and increased developer productivity.
ASPM evaluates the risk associated with each application, gives prioritization using graph-based methods including attack path analysis. To see how graph analytics help with your security strategy, try our forever-free Developer Edition or book a demo with our team.
Get started with PuppyGraph!
Developer Edition
- Forever free
- Single noded
- Designed for proving your ideas
- Available via Docker install
Enterprise Edition
- 30-day free trial with full features
- Everything in developer edition & enterprise features
- Designed for production
- Available via AWS AMI & Docker install






