What is Cloud SIEM? Solutions and Strategies
SIEM (Security Information and Event Management) remains a cornerstone of security operations, helping teams detect, investigate, and respond to threats by centralizing logs and telemetry across their environments. But as infrastructure becomes more cloud-based and distributed, traditional SIEM platforms often struggle to keep up.
Cloud-native SIEM is quickly becoming the preferred choice. According to Google Cloud’s Cybersecurity Forecast 2025, scalability and cost-efficiency are driving widespread adoption, even among organizations that have been hesitant to move away from on-prem deployments.
Still, cloud SIEM is not a one-size-fits-all solution. Many teams continue to rely on traditional SIEMs due to data residency constraints, legacy systems, or specific operational needs. Understanding how SIEM works, both in its classic form and in modern cloud-native implementations, is key to finding the right fit for your infrastructure and design needs.
In this article, we’ll break down what SIEM is and how it’s evolving in the cloud. We’ll explore why cloud SIEM is gaining momentum, what its core components and key features are, and how leading platforms compare in 2025. We’ll also cover common challenges, best practices for implementation, and what to consider as the industry moves further toward cloud-first security.
What is SIEM?
SIEM (Security Information and Event Management) helps security teams collect, analyze, and manage security data across their environment to detect and respond to threats more effectively. By consolidating log data from cloud services, servers, endpoints, and network devices, SIEM provides a centralized view of activity and context for identifying complex threats, providing analysts the information they need to identify complex threats and prioritize high-risk incidents.
A typical SIEM includes log collection, data normalization, correlation engines, detection rules, dashboards, and long-term storage. These components work together to spot suspicious patterns, trigger alerts, and support investigations and compliance requirements. While these functions are common across platforms, how they’re delivered and scaled depends on the deployment model.
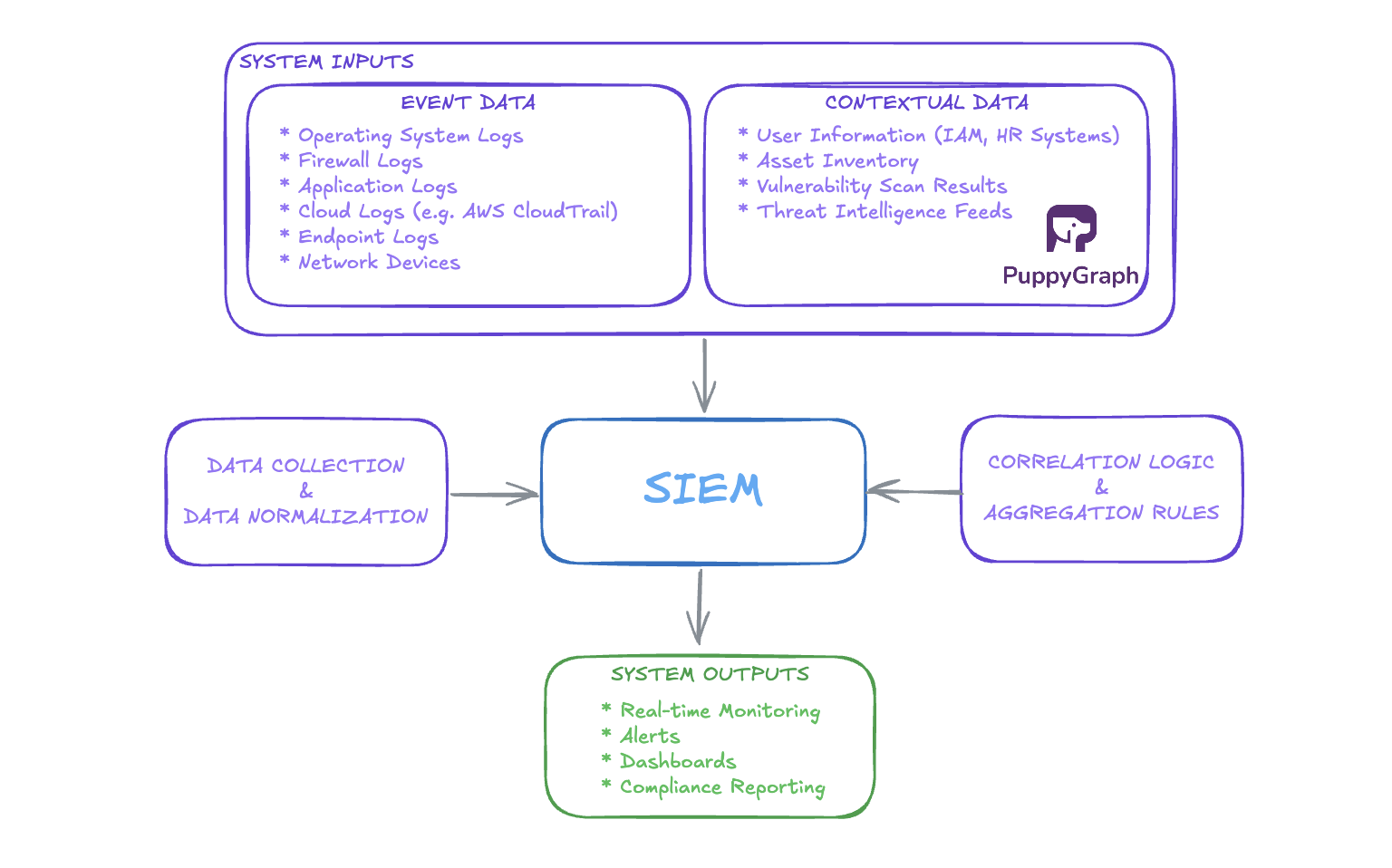
In addition to threat detection and response, SIEM platforms also help meet compliance requirements by enforcing retention policies and generating audit-ready reports for frameworks like SOC 2, HIPAA, PCI DSS, and ISO 27001. They also provide the visibility needed to demonstrate that monitoring and alerting mechanisms are in place, which is often essential for passing audits and maintaining certification. For organizations in regulated industries, this compliance support is often one of the primary reasons for adopting SIEM.
SIEM has become a key part of how security teams structure their day-to-day operations. It acts as a central layer that connects data from across tools and environments, helping analysts see the bigger picture. Rather than working in isolated systems or reacting to siloed alerts, teams can use SIEM to coordinate efforts, streamline investigations, and improve decision-making over time.
What is Cloud SIEM?
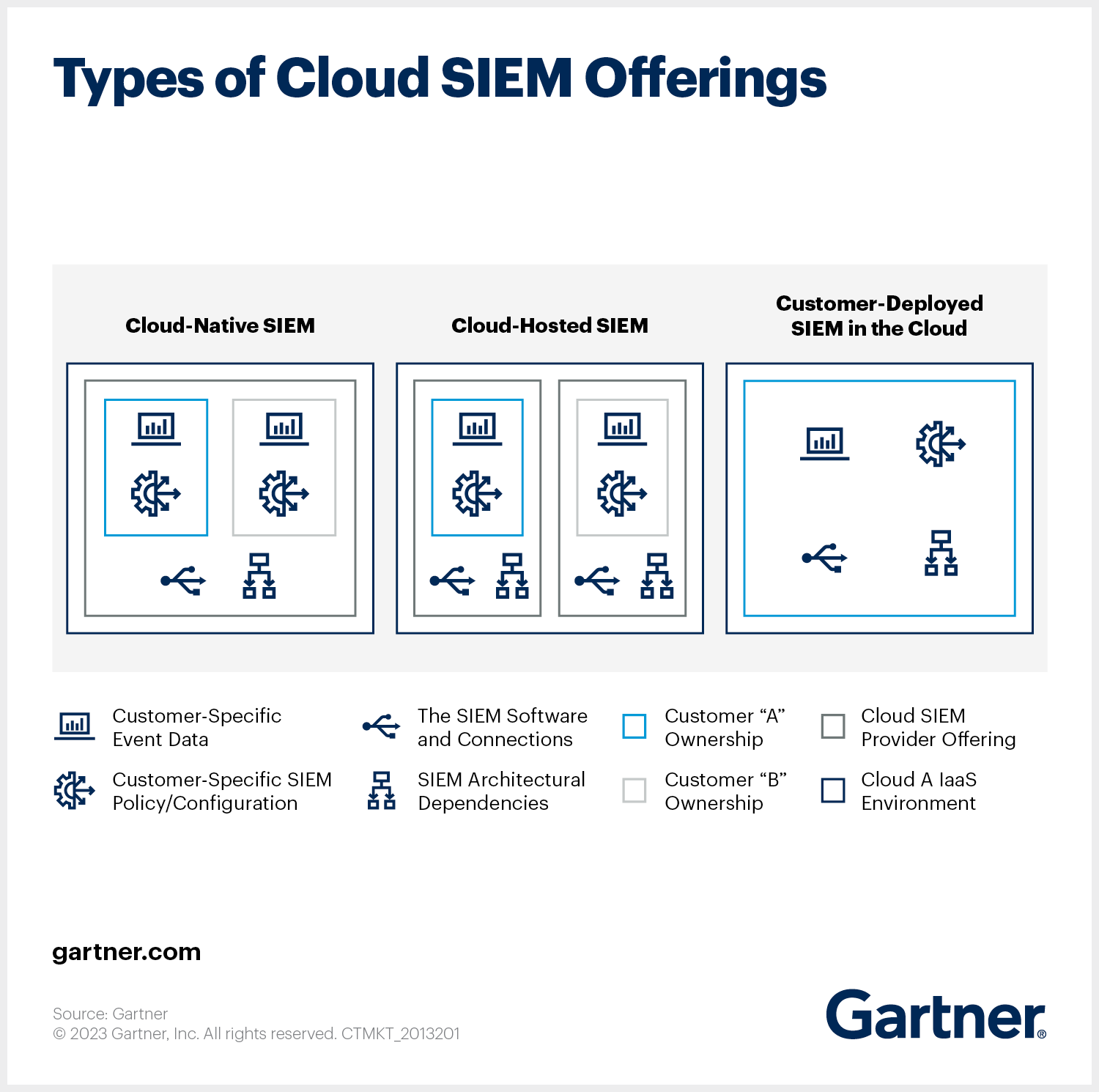
Cloud SIEM refers to security information and event management platforms delivered in the cloud. While often treated as a single category, there are three primary delivery models: cloud-native, cloud-hosted, and customer-deployed. These differ from deployment methods like on-prem and hybrid, which we cover in more detail in our SIEM architecture blog.
Cloud-native SIEM
Cloud-native SIEM platforms are purpose-built for the cloud. They scale on demand, support real-time ingestion, and integrate with cloud services. Most use a multi-tenant architecture, though many vendors offer single-tenant deployments for organizations with stricter compliance or data isolation needs. These platforms typically include elastic storage and built-in connectors for AWS, Azure, Google Cloud, and major SaaS tools. With infrastructure, scaling, and updates fully managed by the vendor, security teams can focus on detection, investigation, and response without worrying about backend upkeep.
Some are also available as managed services, offering operational support directly from vendors or partners, a model particularly suited to the centralized, API-driven nature of cloud-native platforms.
Cloud-Hosted SIEM
Cloud-hosted SIEM platforms are traditional systems deployed in a cloud environment, often managed by the vendor or hosted on IaaS platforms. They eliminate the need for on-prem hardware but generally retain a legacy architecture, which can limit scalability and integration speed compared to cloud-native designs.
This model appeals to teams looking to reduce infrastructure overhead without fully reworking their SIEM stack. It's a common middle ground for organizations moving off on-prem systems while maintaining familiarity with existing tools.
Customer-Deployed Cloud SIEM
In this model, the organization deploys and manages the SIEM platform in its own cloud environment (e.g., AWS, Azure, GCP). Unlike vendor-hosted options, the customer is responsible for setup, scaling, maintenance, and updates. This offers full control over the system while avoiding physical infrastructure.
Customer-deployed SIEM can be attractive for teams with specific compliance or data residency needs, or those with existing DevOps capabilities. However, it requires significant operational effort and tends to lack the automation, elasticity, and support found in vendor-managed models.
Why Cloud SIEM is Critical Today
Scales with Modern Infrastructure
Cloud SIEM platforms are built for dynamic, distributed environments. They ingest high volumes of data from cloud workloads, remote endpoints, and SaaS apps in near real time. This scalability becomes crucial during incidents that generate sudden spikes in telemetry such as credential stuffing attacks, privilege escalation, or lateral movement across cloud accounts. Traditional SIEMs often struggle to handle this burst traffic without lag, dropped events, or performance degradation. In contrast, cloud-native platforms scale elastically, adapting to load fluctuations without requiring manual intervention or reconfiguration.
Faster Setup and Easier Integration
Many cloud SIEM solutions reduce onboarding time with auto-discovery and prebuilt connectors for major cloud and identity platforms. These features simplify integration, especially in environments where APIs expose infrastructure and access configurations automatically. Some offer agentless data collection and auto-discovery of assets, especially in cloud environments where APIs can surface infrastructure, storage, and identity configurations automatically. These capabilities are far more limited in on-premise environments, making cloud SIEM the primary beneficiary of this kind of automation.
Less Overhead and More Cost Control
Because infrastructure, storage, and maintenance are handled by the vendor, cloud SIEM reduces the operational burden on security teams. There’s no need to provision hardware, monitor capacity, or manage system upgrades, which allows teams to stay focused on detection, investigation, and response. Most cloud SIEMs use usage-based pricing, which makes them accessible to smaller organizations and easier to scale. While costs can grow quickly with high data volumes or noisy log data, strategies like tuning retention policies and filtering low-value data help keep costs predictable.
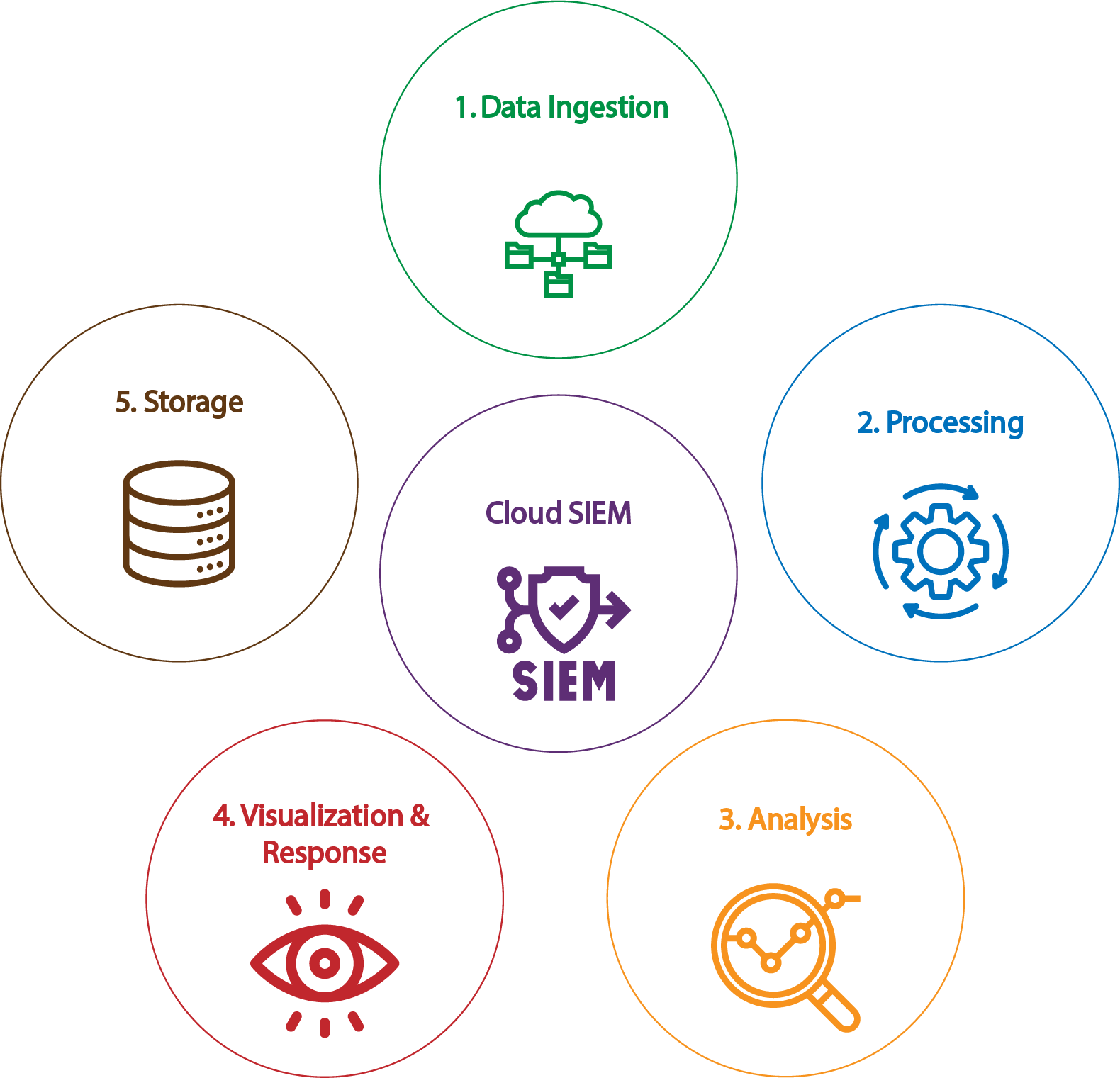
Core Components of Cloud SIEM
Cloud SIEM platforms share the same foundational components as traditional SIEM systems, but the way these components are delivered and scaled is fundamentally different. Each function, from ingestion to search, has been built to handle the volume, speed, and complexity of today’s infrastructure. For a detailed breakdown of how traditional SIEM architecture works, see our SIEM architecture blog. In this section, we’ll focus on how each core component functions in a cloud-native SIEM and how it compares to its on-premise counterpart.
Data Collection
Cloud SIEMs streamline data collection through out-of-the-box support for modern infrastructure, identity systems, and SaaS applications. Unlike traditional SIEMs, which often rely on custom agents, these platforms can ingest telemetry from distributed sources with minimal setup. This enables faster onboarding and ingestion across distributed environments.
Processing
In traditional SIEMs, processing is often constrained by local infrastructure and rigid parsing rules. Cloud SIEMs handle this step in near real time using scalable pipelines that normalize log formats and enrich events with context such as user roles, asset types, and geolocation. Once processed, the data flows into the analytics layer.
Analysis
Cloud SIEM platforms can correlate and analyze events using distributed processing and often integrate advanced techniques like machine learning. These systems can scan for patterns across billions of events, linking related activity into threat narratives. Some platforms also support behavior analytics or MITRE ATT&CK mapping to surface more nuanced threats that go beyond simple rule matches.
Visualization and Response
Dashboards in cloud SIEMs are typically interactive, real-time, and customizable. Analysts can track high-level trends, drill into specific incidents, and pivot across time ranges or attributes without writing complex queries. Many platforms also integrate with SOAR tools or provide built-in automation to trigger alerts, assign tickets, or execute response actions based on severity and playbook logic.
Storage
Cloud SIEMs use vendor-managed, elastic storage that scales automatically with data growth. Teams no longer need to provision hardware or monitor capacity, as storage expands with demand. Long-term retention policies can be applied to meet compliance requirements without degrading performance. This solves a major challenge of on-premise SIEMs, where limited storage often forces teams to drop logs or shorten retention windows.
Key Features to Look for in a Cloud SIEM
Cloud SIEM solutions vary widely in capabilities, pricing, and performance. While many offer similar core functions, the best tools stand out by how well they handle scale, complexity, and day-to-day security operations. When evaluating cloud SIEM vendors, it’s worth considering features that affect how well the platform fits your environment and scales over time.
Advanced Analytics and Real-Time Detection
Effective threat detection goes beyond simple rule matching. Cloud SIEM solutions should support behavioral analytics, MITRE ATT&CK mapping, and both batch and stream processing. These capabilities help uncover stealthy, multi-stage attacks and reduce false positives, giving teams faster, more accurate security insights.
Administration, Manageability, and Compliance
The best Cloud SIEMs make it easy to manage users, rules, and data at scale. Look for role-based access controls, centralized rule editing, and automation around log lifecycle management. Many also come with built-in support for compliance frameworks like SOC 2, PCI, and HIPAA, helping teams meet regulatory requirements without additional tooling.
Ecosystem Integration
Before committing to a solution, make sure the vendor supports ingestion from the data sources most critical to your operations. Some tools may require custom connectors or lack support for specific log formats, so it’s important to understand where the product’s integration capabilities might fall short. Broad, reliable integration coverage not only improves visibility but also reduces operational overhead and accelerates response workflows.
Operational Usability and Predictable Cost
Usability matters. A good Cloud SIEM should have responsive dashboards, fast search, and workflows that support investigation and triage. It should also be cost-transparent, with pricing models that make it easy to understand usage and avoid surprise overages. Look for features like usage dashboards, ingestion controls, and budget alerts to stay ahead of spend.
Top Cloud SIEM Solutions (2025)
The best SIEM for your team depends on how well it integrates with your infrastructure and supports your goals. Many leading platforms offer free trials or demos, making it easier to test performance, integrations, and usability before committing. Below are five top-rated cloud SIEM solutions in 2025, each with distinct strengths and evaluation options.
CrowdStrike Falcon Next-Gen SIEM

Best for: AI-driven detection and response in hybrid environments
- Delivery Model: Fully cloud-native (SaaS on the Falcon platform)
- Strengths: Unified visibility across endpoint, identity, and SIEM; native threat intelligence; autonomous workflows
- Considerations: Works best when used with other Falcon modules
- Pricing: Subscription-based; bundled with Falcon
- Try it: Free trial available
Microsoft Sentinel

Best for: Teams operating primarily in the Microsoft ecosystem
- Delivery Model: Fully cloud-native (SaaS on Azure)
- Strengths: Tight integration with Microsoft Defender, Entra, and Azure services; built-in SOAR
- Considerations: Can become expensive with high ingestion; Azure expertise often required
- Pricing: Consumption-based (per GB), with reserved capacity options
- Try it: Free trial available
Google Chronicle

Best for: Long-term data retention and large-scale search
- Delivery Model: Fully cloud-native (SaaS on Google Cloud)
- Strengths: Petabyte-scale querying; fixed-cost ingestion; strong Google Cloud integration
- Considerations: Limited built-in SOAR; may require custom ingestion for non-Google sources
- Pricing: Tiered by ingestion and source volume
- Try it: Contact for Demo
Exabeam Fusion

Best for: Teams prioritizing behavioral analytics and SOAR integration
- Delivery Model: Fully cloud-native
- Strengths: Strong SOAR integration, good for threat hunting and case management
- Considerations: Powerful but can be time-consuming to deploy; onboarding may require upfront investment and tuning
- Pricing: Custom pricing based on users or data sources
- Try it: Request a POV
Securonix

Best for: Insider threat detection and identity-centric use cases
- Delivery Model: Fully cloud-native SaaS
- Strengths: Flexible deployment; robust detection tools; identity-focused telemetry support
- Considerations: Mixed onboarding/support reviews; some users report learning curve
- Pricing: Event-volume based; quotes required
- Try it: Contact for Demo
Challenges with Cloud SIEM
Alert Fatigue and False Positives
Cloud SIEMs improve visibility across environments, but they often generate more alerts than teams can realistically investigate. Broad correlation logic and static rules that trigger on low-priority activity can overwhelm Security Operations Center (SOC) teams with noise, slowing down response times. As a result, serious threats become harder to detect and contain, weakening the organization’s overall security posture.
Cost Management
Most cloud SIEMs use consumption-based pricing tied to data ingestion or storage. While this model offers flexibility, costs can spike during incident investigations, burst traffic, or over-collection of low-value logs. Without usage controls, budget visibility, or tiered retention strategies, it’s easy to run into surprise bills.
Vendor Lock-In
Moving to a cloud-native SIEM often means adopting that vendor’s logging format, storage model, and response workflows. Migrating away, or even integrating deeply with another ecosystem, can be slow and costly. Some platforms offer APIs and export features, but true portability is still limited across the board.
Detection Gaps in Complex Environments
Even with machine learning and unified visibility, many cloud SIEMs still miss complex threats without deeper context, especially those that unfold across multiple systems. Static rules and behavior models can detect isolated anomalies, but they often fail to uncover relationships between events like lateral movement, privilege escalation paths, or coordinated access patterns.
Best Practices for Cloud SIEM
Define Clear Objectives and Use Cases
Before configuring alerts or connecting data sources, it’s important to define what success looks like for your organization. What risks are most critical? What types of threats are you trying to detect? Which compliance frameworks do you need to support? These answers should drive how you configure, tune, and prioritize your SIEM. No two organizations have the same threat model or operational constraints, and the value of a cloud SIEM depends on how well it aligns with your specific goals, infrastructure, and security maturity.
Start with High-Value Data Sources
Resist the urge to connect everything out of the gate. Begin with critical security data that offer high signal with manageable volume like authentication logs, admin activity, and cloud audit trails. This allows teams to build confidence in detections and reduce early-stage alert fatigue.
Implement Ingestion and Cost Controls
Cloud SIEM pricing often scales with ingestion. Use filters, quotas, and budget alerts to stay ahead of surprises. Monitoring ingestion trends can also reveal issues like misconfigured integrations or unexpected behavior during incidents.
Normalize and Aggregate Data
Inconsistent log formats can make it hard to detect and correlate threats. Normalization ensures fields like user, IP, and action are standardized across sources, while aggregation reduces noise and highlights meaningful patterns. Done right, this improves detection accuracy and makes alerts easier to trust.
Review and Tune Detections Regularly
Default rules often need refining to match your environment and reduce false positives. Schedule regular reviews of alert logic and detection patterns to ensure they reflect current risks, infrastructure changes, and evolving attacker behavior.
How PuppyGraph Enhances Cloud SIEM
Earlier, we touched on how cloud SIEMs can struggle to connect the dots across distributed systems. Even with machine learning and centralized security data, it’s not always clear how isolated events relate or whether they add up to something more serious. Complex attacks like lateral movement or chained privilege escalations can still slip through, even with machine learning and behavior-based detection.
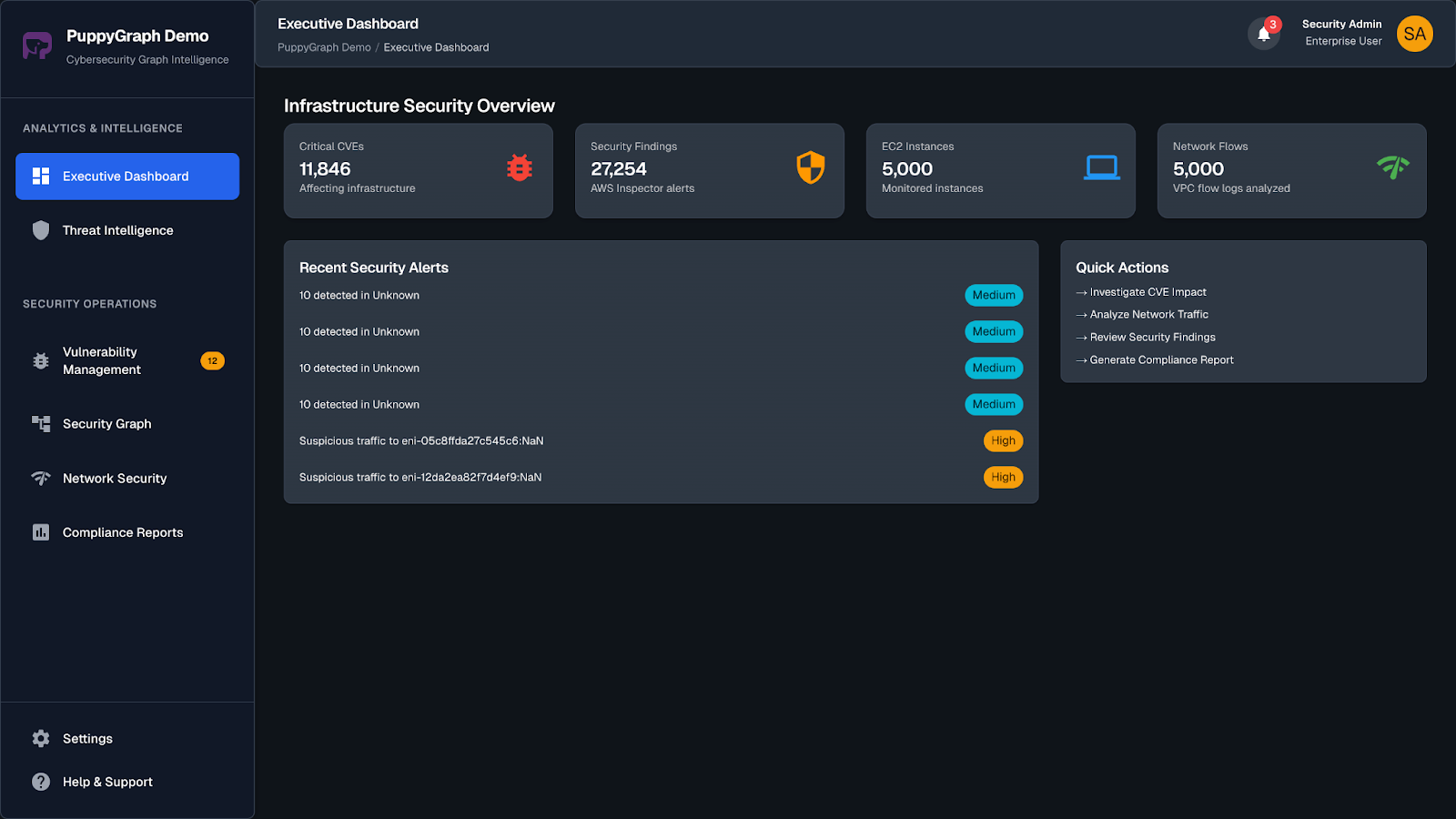
PuppyGraph brings graph analytics into the picture to surface those connections. Rather than replacing your SIEM, it enhances it by revealing how users, systems, and events interact over time.
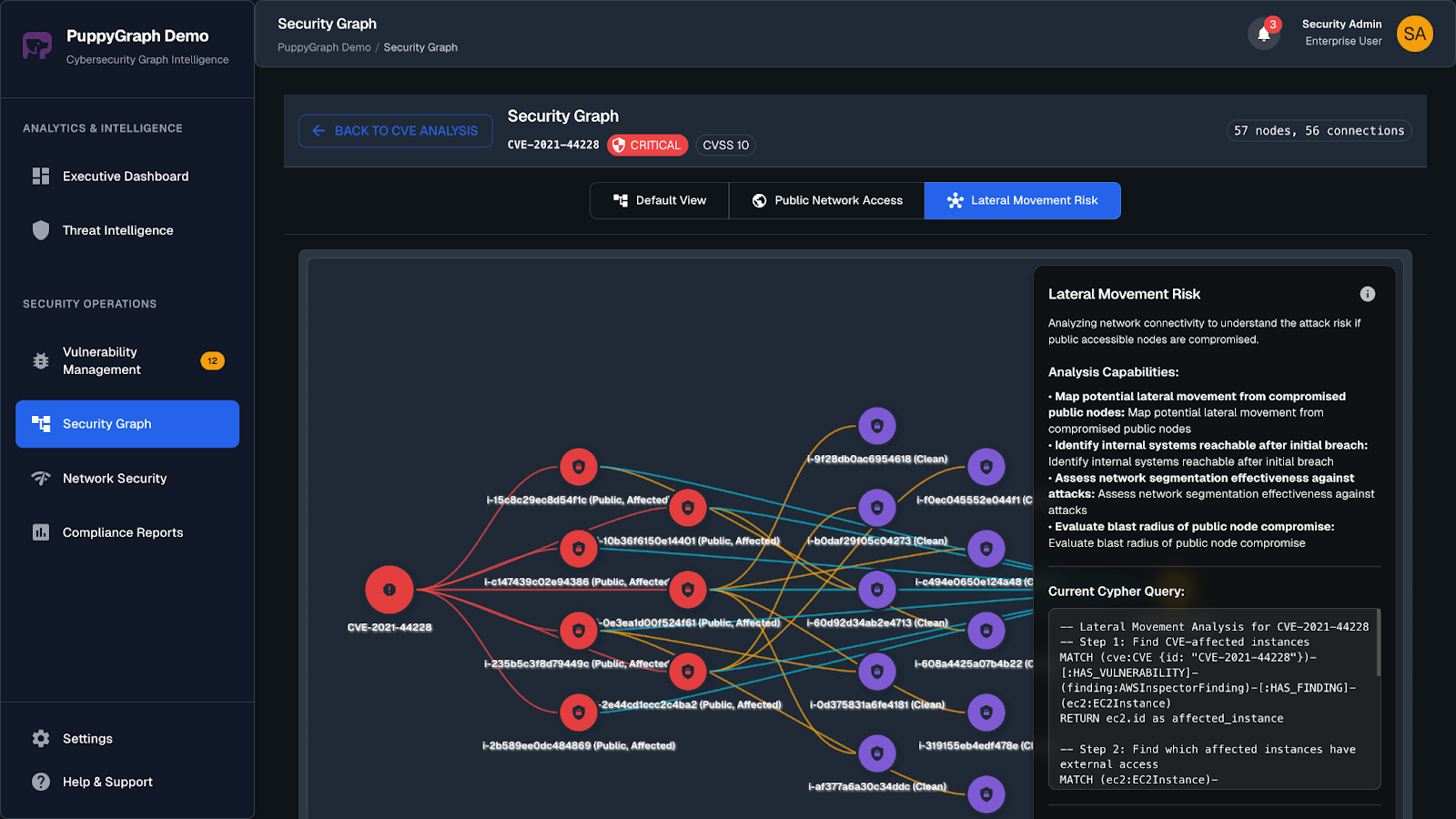
- Zero ETL: No need to move or duplicate data. PuppyGraph connects directly to your existing data sources without complex transformation pipelines.
- Full control: Your data stays where it is. PuppyGraph runs on top of your existing architecture, so you keep full ownership and governance.
- Flexible graph modeling: Model entities and relationships in a way that fits your environment. Iterate quickly as your understanding evolves.
- Scalable and performant: Designed for large security datasets and real-time exploration, without sacrificing speed.
- User-friendly interface: Analysts can explore graphs without writing complex queries, making relationship-based detection more accessible to security teams.
Conclusion
As cloud adoption accelerates, SIEM remains a critical layer in securing modern infrastructure. Whether deployed as a cloud-native platform or integrated into hybrid environments, the effectiveness of a cloud SIEM depends on how well it fits your organization’s needs, infrastructure, and goals. Choosing the right solution requires understanding your use cases, evaluating trade-offs across delivery models, and balancing detection capabilities with cost and operational complexity.
For teams looking to enhance their SIEM with deeper context and more flexible analytics, graph technology can offer a meaningful advantage. If you're exploring graph analytics without the overhead of data duplication or specialized infrastructure, try the forever-free PuppyGraph Developer Edition or book a demo to see how easily you can start querying your existing data as a graph.
Get started with PuppyGraph!
Developer Edition
- Forever free
- Single noded
- Designed for proving your ideas
- Available via Docker install
Enterprise Edition
- 30-day free trial with full features
- Everything in developer edition & enterprise features
- Designed for production
- Available via AWS AMI & Docker install






